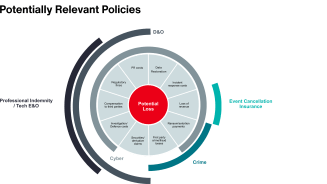
On July 19, 2024, a security update issued by CrowdStrike caused an IT outage, disrupting global business operations. While initial fears of a major cyber attack proved to be unfounded, the event’s impact was significant, demonstrating potential vulnerabilities in organizations’ operational and cyber resilience.
In response to the CrowdStrike outage, businesses should review their crisis management frameworks, with a focus on these five lessons learned to build sustained cyber resilience. Doing so will help businesses identify, assess, mitigate and transfer cyber risk and be better prepared to recover should an attack occur.
1. Put Incident Response Plans to the Test
Having a well-prepared and defined incident response plan is crucial for mitigating the impacts of IT disruptions and cyber attacks. However, the truest measure of plan effectiveness is how it performs when tested in real-world scenarios.
The CrowdStrike outage provided businesses with an opportunity to evaluate the efficacy of their plan and consider what improvements can be made. A key factor of an incident response plan is knowing when it should be activated. In this case, the outage demonstrated the need for clear activation thresholds that are understood by high level decision-makers in the organization, who are then able to assess the situation and trigger the plan appropriately. This is essential for minimizing business impact and maintaining operations.
During an Aon webinar held one week after the event, 83 percent of those polled reported having an incident response plan in place, and 76 percent said it performed well following the CrowdStrike outage. These figures are encouraging, but also highlight a potential resilience gap that could become critical when a threat is more severe or consequential. Businesses that take the time to run a risk assessment to review how their operations responded to the CrowdStrike outage may be better positioned to handle the next one.
Even for organizations not directly affected by the outage — of those polled, 32 percent were indirectly impacted, compared to 30 percent who were directly impacted — there are lessons to be learned on potential supply chain vulnerabilities. This underscores the need to review third party relationships and interdependencies when developing and improving contingency plans.