
Support

Stroz Friedberg Digital Forensics and Incident Response has observed an uptick in SIM swapping across multiple industries, with several recent incidents targeting crypto and crypto-adjacent companies. This increasing trend has been noted by the FBI in their internet crime report, with 1,611 complaints reported in 2021 and 2,026 complaints reported in 20221.
While SIM swap attacks are sometimes employed to gain unauthorized access to an individual’s personal email or cryptocurrency wallet, their impact becomes significant when leveraged to breach corporate network accounts. Whether aimed at bypassing multi-factor authentication (MFA) or resetting passwords, these attacks can leave companies with unexpected vulnerabilities. Notably, SIM swapping has been observed as an initial access technique in business email compromise incidents, which constitute a substantial portion of the incidents faced by organizations.
This post will provide an overview of SIM swapping techniques, discuss recent events that Stroz Friedberg has observed related to SIM swapping attacks, and provide detection methods and mitigations against this threat.
Historically, SIM cards have contained sensitive user data such as phone numbers, security keys, contact lists, email accounts, social media profiles, and financial banking information2. These days SIM cards contain much less data and are primarily used to link a phone number to a device. A SIM swap attack is ultimately successful when a user’s phone number has been transferred to a SIM card controlled by the threat actor. SIM swapping leaves users unable to access accounts, make phone calls, or send texts.
Threat actors can obtain a target’s phone number through spear phishing, third-party breach databases, or free public resources such as data aggregator sites or social media. Therefore, individuals with a greater online presence may experience a higher risk for becoming the target of a SIM swap attack. Individuals should consider investing in greater individual privacy to help reduce the amount of information that is publicly and easily available.
Threat actors can use various methods to initiate a SIM swap attack, including but not limited to:
Once a threat actor takes control of the target’s phone number, this provides multiple opportunities for further exploitation or achieving their objectives. This includes the ability to reset passwords and/or receive MFA authentication codes via SMS.
Sample SIM swap attack workflow
SIM swapping attacks are frequently used to compromise email accounts and single sign-on accounts with access to various applications, giving threat actors access to cloud storage and other sensitive organizational information. Targets may be at a greater risk if the user has access to administrative privileges or more applications than the average user. The following sections detail attack patterns identified in recent Stroz Friedberg matters involving SIM swapping.
In contrast with common usage of SIM swapping as an MFA bypass technique, Stroz Friedberg’s analysis has found that threat actors are using SIM swaps to reset passwords without having the user’s credentials.
Threat actors may execute a series of password reset attempts on multiple accounts in quick succession, assessing the feasibility of exploiting SMS verification for password recovery. During the password reset process on widely used platforms such as Microsoft 365, malicious actors can identify the verification methods configured for a specific account. If SMS verification is active, they may also gain access to the last few digits of the associated phone number. In some cases, this reconnaissance on targeted accounts occurred several weeks prior to the actual SIM swap attack.
Upon successful completion of the SIM swap, the threat actor can reset the user’s password to compromise the account without ever having the user’s original password.
Many of these incidents have included rapid and noisy post-compromise activity. The threat actor has little incentive to act in a covert manner because a SIM swap is immediately observable to the target user. In addition to being notified by the carrier, users typically notice quickly that they are locked out of their account or have lost access to their mobile service. After a SIM swap, the threat actor often enters the account and downloads sizable quantities of data in a short period of time from cloud storage or other data-driven applications, such as Microsoft SharePoint and OneDrive. By the time the organization has removed the threat actor’s access, the threat actor already possesses the organization’s information.
Mobile forensic artifacts typically lack conclusive evidence of SIM swapping. However, many wireless carriers provide notifications to alert users before their number is swapped to another device.
Forensic examiners can review a mobile device for evidence of text messages containing these notifications. These notifications have been observed when:
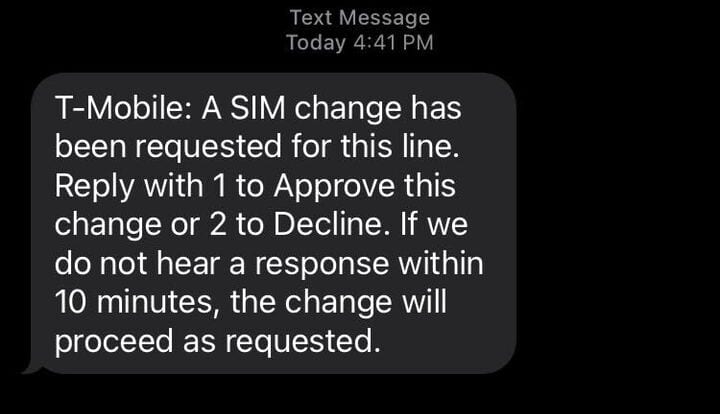
Example of a SIM swapping notification received from a wireless carrier
Some threat actors have inundated their target with a high volume of text messages around the time when the wireless carrier sends out its notification. Stroz Friedberg analysis has shown users receiving a large quantity of automated messages from various companies, likely intended to divert the target’s attention away from the carrier’s SIM swap notifications. Threat actors may generate these messages from websites capable of initiating text messages to a specified phone number, such as one-time passwords or invitations for mobile application installations.
There are various detection methods to identify SIM swapping attacks or the resulting compromise that can help to alert either the user or the organization about unusual activity which include:
Individuals and organizations can protect themselves against SIM swapping attacks using the methods below:

Support
About Cyber Solutions:
Aon’s Cyber Solutions offers holistic cyber risk management, unsurpassed investigative skills, and proprietary technologies to help clients uncover and quantify cyber risks, protect critical assets, and recover from cyber incidents.
General Disclaimer
This document is not intended to address any specific situation or to provide legal, regulatory, financial, or other advice. While care has been taken in the production of this document, Aon does not warrant, represent or guarantee the accuracy, adequacy, completeness or fitness for any purpose of the document or any part of it and can accept no liability for any loss incurred in any way by any person who may rely on it. Any recipient shall be responsible for the use to which it puts this document. This document has been compiled using information available to us up to its date of publication and is subject to any qualifications made in the document.
Terms of Use
The contents herein may not be reproduced, reused, reprinted or redistributed without the expressed written consent of Aon, unless otherwise authorized by Aon. To use information contained herein, please write to our team.
Our Better Being podcast series, hosted by Aon Chief Wellbeing Officer Rachel Fellowes, explores wellbeing strategies and resilience. This season we cover human sustainability, kindness in the workplace, how to measure wellbeing, managing grief and more.
Expert Views on Today's Risk Capital and Human Capital Issues
Expert Views on Today's Risk Capital and Human Capital Issues
Expert Views on Today's Risk Capital and Human Capital Issues
The construction industry is under pressure from interconnected risks and notable macroeconomic developments. Learn how your organization can benefit from construction insurance and risk management.
Stay in the loop on today's most pressing cyber security matters.
Our Cyber Resilience collection gives you access to Aon’s latest insights on the evolving landscape of cyber threats and risk mitigation measures. Reach out to our experts to discuss how to make the right decisions to strengthen your organization’s cyber resilience.
Our Employee Wellbeing collection gives you access to the latest insights from Aon's human capital team. You can also reach out to the team at any time for assistance with your employee wellbeing needs.
Explore Aon's latest environmental social and governance (ESG) insights.
Our Global Insurance Market Insights highlight insurance market trends across pricing, capacity, underwriting, limits, deductibles and coverages.
How do the top risks on business leaders’ minds differ by region and how can these risks be mitigated? Explore the regional results to learn more.
Our Human Capital Analytics collection gives you access to the latest insights from Aon's human capital team. Contact us to learn how Aon’s analytics capabilities helps organizations make better workforce decisions.
Explore our hand-picked insights for human resources professionals.
Our Workforce Collection provides access to the latest insights from Aon’s Human Capital team on topics ranging from health and benefits, retirement and talent practices. You can reach out to our team at any time to learn how we can help address emerging workforce challenges.
Our Mergers and Acquisitions (M&A) collection gives you access to the latest insights from Aon's thought leaders to help dealmakers make better decisions. Explore our latest insights and reach out to the team at any time for assistance with transaction challenges and opportunities.
How do businesses navigate their way through new forms of volatility and make decisions that protect and grow their organizations?
Our Parametric Insurance Collection provides ways your organization can benefit from this simple, straightforward and fast-paying risk transfer solution. Reach out to learn how we can help you make better decisions to manage your catastrophe exposures and near-term volatility.
Our Pay Transparency and Equity collection gives you access to the latest insights from Aon's human capital team on topics ranging from pay equity to diversity, equity and inclusion. Contact us to learn how we can help your organization address these issues.
Forecasters are predicting an extremely active 2024 Atlantic hurricane season. Take measures to build resilience to mitigate risk for hurricane-prone properties.
Our Technology Collection provides access to the latest insights from Aon's thought leaders on navigating the evolving risks and opportunities of technology. Reach out to the team to learn how we can help you use technology to make better decisions for the future.
Trade, technology, weather and workforce stability are the central forces in today’s risk landscape.
Our Trade Collection gives you access to the latest insights from Aon's thought leaders on navigating the evolving risks and opportunities for international business. Reach out to our team to understand how to make better decisions around macro trends and why they matter to businesses.
With a changing climate, organizations in all sectors will need to protect their people and physical assets, reduce their carbon footprint, and invest in new solutions to thrive. Our Weather Collection provides you with critical insights to be prepared.
Our Workforce Resilience collection gives you access to the latest insights from Aon's Human Capital team. You can reach out to the team at any time for questions about how we can assess gaps and help build a more resilience workforce.

Cyber Labs 3 mins
This client alert provides an overview of the current global IT outage that is related to a CrowdStrike update. We provide an overview of CrowdStrike's response and guidance, and Aon Cyber Solutions' recommendations for affected clients.