
Support

Industrial control systems are crucial for managing critical infrastructure. The growth of Industry 4.0 and Industrial Internet of Things (IIoT) heightens the vulnerability of these systems to cyber threats. Industrial Control System (“ICS”) emphasize data availability over integrity and confidentiality, in contrast to IT networks. This distinction requires customized security strategies that address the specific needs and vulnerabilities of ICS environments. The integration of cloud services and virtualization further expands the attack surface, creating exploitable gaps. [1]
Recent research highlights the growing exposure of key ICS communication protocols such as Modbus, KNX, and BACnet, particularly in critical sectors such as manufacturing, utilities, and building automation. Although fewer ICS systems are directly internet-facing, these protocols remain highly vulnerable, especially in North America and Europe. The integration of Operational Technology (“OT”) with IT systems amplifies risks, highlighting the necessity for strong cybersecurity strategies. [2]
The assertion that an 'air gap' constitutes a foolproof security approach is misleading. While network segmentation can create security zones, achieving complete network separation is virtually impossible today. Modern systems often include wireless diagnostics and removable media, which can bypass air gaps. In addition, this myth overlooks the threat from insiders, authorized users who can cause harm. To effectively protect ICS environments, organizations must move beyond relying solely on air gaps and adopt a multilayered security approach, including continuous monitoring, employee training, and incident response planning [3].
In January 2024, Shodan identified nearly 110,000 ICS devices [2], including more than 6,500 publicly exposed programming logic controllers (“PLC”), accessible online and using protocols such as Modbus and Siemens S7 [4]. These exposures lead to targeted attacks, such as those by the Iranian hacktivist group Cyber Av3ngers [5], [6], who attacked Unitronics PLCs globally, including at a water utility near Pittsburgh and a small water utility in Ireland, causing a two-day water supply disruption. [7]
To improve ICS security, we strongly urge the implementation of these decisive actions [8]:
For OT/ICS systems not directly exposed, attackers often employ more sophisticated methods to infiltrate networks. They might start with phishing or watering hole attacks to gain initial access, followed by exploiting software vulnerabilities or using social engineering techniques. Once inside, attackers can move laterally, compromising operational computers, databases, manipulating data, or targeting communication between PLCs and field equipment. The most severe threats occur when attackers gain direct physical access or remote control over critical components, enabling destructive actions such as firmware modification or sabotage.
While many attacks on ICS are financially motivated, others are driven by hacktivist groups and can escalate into complex operations involving espionage or sabotage. Espionage-driven attacks focus on gathering sensitive information or intellectual property, using advanced malware and social engineering to remain undetected. Financially motivated attacks may involve direct tampering, unauthorized system use, or manipulating physical parameters (e.g., temperature or pressure) to cause damage or alter production output.
The sophistication of cyber threats has grown with the emergence of rootkits, digitally signed obfuscated malwares, and the commercialization of 0-day vulnerabilities. The increasing risks from AutoRun malware, remote access attacks, and the rise of "hacking as a service" underscore the urgent need for robust cybersecurity actions. These services make advanced malwares and cyberattacks more accessible, emphasizing the need for strengthened defenses. In this evolving threat landscape, it is strongly recommended that organizations implement comprehensive strategies to protect their ICS assets from increasingly sophisticated threats. [1], [9]

Support
The maritime industry, crucial for global trade and economic stability, is increasingly targeted by sophisticated cyberattacks. As ships and ports become more connected through digital systems, they are becoming more targets for cyber threats that take advantage of the unique ways that maritime technology works. The industry has seen a large increase in cybersecurity breaches, especially in operational technology as it becomes more digital. A research study shows a 900% increase [10] in these breaches, highlighting the increasing risks as ships become more connected to the Internet.
Autonomous ships present new opportunities for cyberattacks within the maritime industry. Currently limited to smaller vessels, they are expected to be used in global shipping by 2030, increasing the risk [49]. These ships rely on sensors and communication systems, making them prime targets for hackers. Past attacks on navigation systems, such as ECDIS and GPS, have shown how vulnerable these systems are. As autonomous ships become more common, they introduce new risks. One major concern is the potential for compromised vessels to be used as weapons. [11]
Although traditional cyber threats [12], [13] such as phishing and ransomware [14], [15] continue to pose significant risks, the advent of specialized malware specifically designed for maritime systems represents an escalating concern. These advanced threats have the potential to infiltrate critical control systems, such as the Steering Gear Control System (“SGCS”) [16] as detailed below or compromising the integrity of data displayed on a radar system [17]. This type of infiltration can lead to catastrophic outcomes like collisions or groundings, reminiscent of the Ever Given incident [18] in the Suez Canal. Recognizing these vulnerabilities and formulating robust defense strategies are essential for protecting the maritime sector from advancing cyber threats.
Key Vulnerabilities in Maritime Systems:
Exploring Advanced Standalone Malware Targeting Maritime SGCS: A Realistic Simulation
Researchers developed and tested malware targeting the Steering Gear Control System on modern ships in a realistic simulation under typical maritime constraints, such as 4 GB of RAM and two CPU cores limited to 5% utilization. The malware autonomously manipulated the SGCS by injecting malicious Modbus packets, exploiting vulnerabilities in protocols such as NMEA 0183 and Modbus. It caused unintended steering changes, posing serious navigational risks. [16]
Such an attack could result in incidents like collisions or groundings, as demonstrated by the Ever Given case. [20] This underscores the need for defense-in-depth cybersecurity strategies, regular vulnerability assessments, comprehensive training, and advanced monitoring tools for early threat detection and response.
The rapid expansion of space technology and the surge in satellite deployments [21] for communication, navigation, and surveillance have dramatically increased the surface area for potential cyberattacks. As nations and private companies race to launch satellites, the complexity and number of systems in space have grown, but cybersecurity measures have lagged behind. Many satellites utilize commercial components [22], [23] that often lack space-grade security, thereby heightening vulnerabilities.
Developing and launching a satellite can take decades, yet they remain in orbit while technology and cybersecurity threats evolve rapidly. This mismatch leaves both satellites and their ground stations exposed to sophisticated attacks that could disrupt critical services worldwide, including GPS, communication, and military operations.[24]
The Potential Consequences of a Satellite Hack
If a satellite is hacked, the consequences could be dire, affecting not only the targeted satellite, but potentially disrupting critical services globally. An adversary might compromise a satellite's propulsion system, leading to orbital anomalies and the risk of collisions with other satellites. Attackers could jam communication systems, leading to the loss of internet, GPS services, or even military communications. Malicious actors could intercept telemetry information, exploit satellite subsystems, transmit fake data, and gain control over a part of the satellite infrastructure. This would enable them to potentially seize control of satellite infrastructure, leading to the disabling of satellites or even redirecting them for harmful purposes. Significant financial losses and national security risks may arise from such scenarios. Dependent infrastructures may experience cascading failures as a result.
Vulnerabilities in Aerospace Systems and Common Attack Methods
Aerospace systems, including satellites, are vulnerable across four main attack surfaces [25], [43]:
Why Threat Actors Focus on Ground Control
Malicious actors are increasingly targeting the more accessible ground segment, which manages satellite communication. Unlike direct attacks on spacecraft, which require significant resources and are easily detectable due to the power and radio frequencies involved, vulnerabilities in the Space Link Extension (“SLE”) protocol [26], [44], [45] between Control Centres and Ground Stations can be exploited to launch Denial of Service (“DoS”) attacks or manipulate communications [25]. This allows attackers to gain indirect control over satellites, making the ground segment a prime target for cyberattacks.
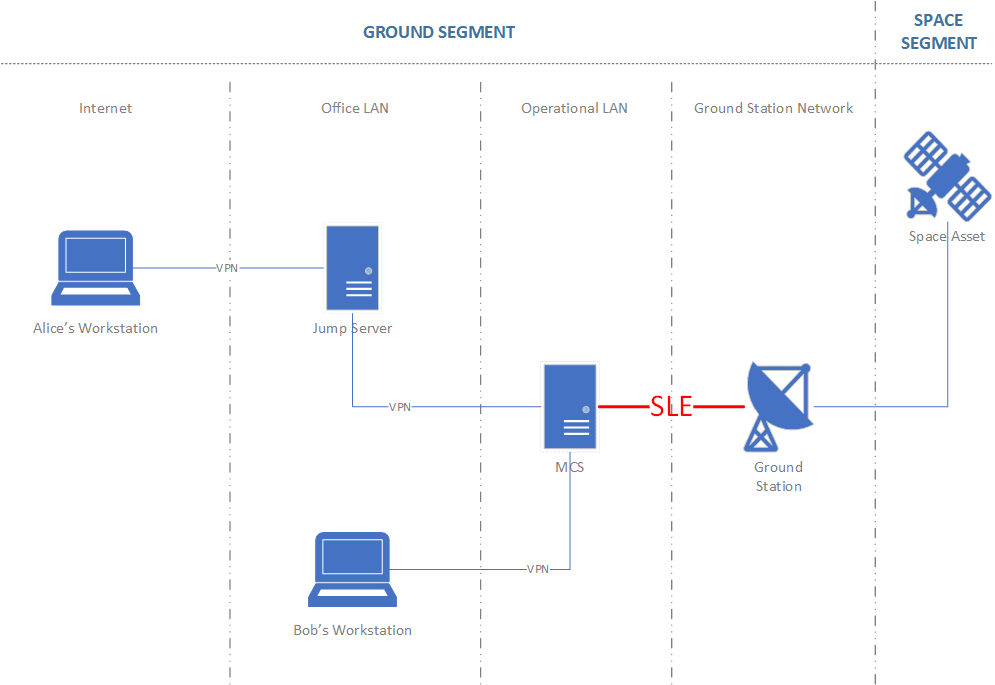
Figure 1: CCSDS SLE Security Communications Threats [44]
The Future of Aerospace Security
As aerospace cyber threats evolve, quantum cryptography is becoming a vital defense, providing virtually unbreakable encryption through quantum key distribution (QKD) [27]. Leading this innovation are the QEYSSat [24], [25] and Eagle-1 [28] satellites, both set for launch between 2025 and 2026, which will advance quantum-secure satellite communications.
In addition, AES-256 encryption [29] and optical inter-satellite links [30], [31], [32] maintain strong security in current systems. SpaceX's Moonlighter satellite [33], [34], designed for cybersecurity testing, enhances real-time defense capabilities. New protocols such as QPEP [34] tackle high-latency encryption, and with satellites integrating into the 5G ecosystem [35], [36], [37], [38], [39], reducing LEO latency and upgrading encryption standards are crucial for securing future global communications.
To understand the impact of cyber threats on critical infrastructure and satellite systems, real-world case studies reveal serious vulnerabilities in the industrial and aerospace sectors. These incidents highlight the urgent need for stronger cybersecurity defenses to protect essential global operations.
The growing threat of cyberattacks on industrial and aerospace systems requires robust defenses. Incidents like Stuxnet and satellite vulnerabilities in conflicts show the real dangers these attacks pose.
Future trends, such as quantum cryptography, AI-driven threat detection, and stronger international cybersecurity standards, will be crucial for securing critical infrastructure. Although risks are high, advanced technology and proactive actions can help protect against these evolving threats.
[1] ‘Securing the Industrial Backbone: Cybersecurity Threats, Vulnerabilities, and Mitigation Strategies in Control and Automation Systems’, Deleted J., vol. 20, no. 7s, pp. 1111–1120, May 2024, doi: 10.52783/jes.3604.
[2] F. R.-V. Labs, ‘The global threat evolution of internet-exposed OT/ICS’, Forescout. Accessed: Aug. 30, 2024. [Online]. Available: https://www.forescout.com/blog/cybersecurity-threat-evolution-of-otics-and-iot-devices/
[3] E. D. Knapp, ‘2 - About Industrial Networks’, in Industrial Network Security (Third Edition), E. D. Knapp, Ed., Syngress, 2024, pp. 11–43. doi: 10.1016/B978-0-443-13737-2.00014-2.
[4] E. López-Morales and U. Planta, ‘SoK: Security of Programmable Logic Controllers’.
[5] Ylabs, ‘GhostSec, the hacktivist collective targeting ICSs’, YLabs. Accessed: Aug. 30, 2024. [Online]. Available: https://labs.yarix.com/2023/08/ghostsec-the-hacktivist-collective-targeting-icss/
[6] ‘Dark Web Profile: Cyber Av3ngers’, SOCRadar® Cyber Intelligence Inc. Accessed: Aug. 30, 2024. [Online]. Available: https://socradar.io/dark-web-profile-cyber-av3ngers/
[7] E. Kovacs, ‘Cyberattack on Irish Utility Cuts Off Water Supply for Two Days’, SecurityWeek. Accessed: Aug. 30, 2024. [Online]. Available: https://www.securityweek.com/cyberattack-on-irish-utility-cuts-off-water-supply-for-two-days/
[8] ‘Exploitation of Unitronics PLCs used in Water and Wastewater Systems | CISA’. Accessed: Aug. 29, 2024. [Online]. Available: https://www.cisa.gov/news-events/alerts/2023/11/28/exploitation-unitronics-plcs-used-water-and-wastewater-systems
[9] E. D. Knapp, ‘3 - Industrial Cybersecurity History and Trends’, in Industrial Network Security (Third Edition), E. D. Knapp, Ed., Syngress, 2024, pp. 45–64. doi: 10.1016/B978-0-443-13737-2.00009-9.
[10] F. Akpan, G. Bendiab, S. Shiaeles, S. Karamperidis, and M. Michaloliakos, ‘Cybersecurity Challenges in the Maritime Sector’, Network, vol. 2, no. 1, Art. no. 1, Mar. 2022, doi: 10.3390/network2010009.
[11] M. Ammar and I. A. Khan, ‘Cyber Attacks on Maritime Assets and their Impacts on Health and Safety Aboard: A Holistic View’, arXiv.org. Accessed: Sep. 04, 2024. [Online]. Available: https://arxiv.org/abs/2407.08406v1
[12] ‘Guidelines on Cyber Security Onboard Ships, Version Four’. Accessed: Aug. 30, 2024. [Online]. Available: https://www.ics-shipping.org/resource/guidelines-on-cyber-security-onboard-ships-version-four/
[13] ‘TransNav Journal - BRAT: A BRidge Attack Tool for Cyber Security Assessments of Maritime Systems’. Accessed: Aug. 30, 2024. [Online]. Available: https://www.transnav.eu/Article_BRAT:_A_BRidge_Attack_Tool_for_Hemminghaus,57,1092.html
[14] ‘1000 Shipping Vessels Impacted by Ransomware Attack - Infosecurity Magazine’. Accessed: Sep. 01, 2024. [Online]. Available: https://www.infosecurity-magazine.com/news/shipping-vessels-ransomware-attack/
[15] K. Tsiakaraki, ‘Cyber security focus: Ransomware attacks is a prominent threat for maritime’, SAFETY4SEA. Accessed: Sep. 01, 2024. [Online]. Available: https://safety4sea.com/cm-cyber-security-focus-ransomware-attacks-is-a-prominent-threat-for-maritime/
[16] G. Longo, F. Lupia, A. Pugliese, and E. Russo, ‘Physics-aware targeted attacks against maritime industrial control systems’, J. Inf. Secur. Appl., vol. 82, p. 103724, May 2024, doi: 10.1016/j.jisa.2024.103724.
[17] G. Longo, E. Russo, A. Armando, and A. Merlo, ‘Attacking (and defending) the Maritime Radar System’, IEEE Trans. Inf. Forensics Secur., vol. 18, pp. 3575–3589, 2023, doi: 10.1109/TIFS.2023.3282132.
[18] S. Editor, ‘Ever Given: The grounding that changed the world’s view of shipping’, SAFETY4SEA. Accessed: Sep. 01, 2024. [Online]. Available: https://safety4sea.com/cm-ever-given-the-grounding-that-changed-the-worlds-view-of-shipping/
[19] O. Polikarovskykh, Y. Daus, D. Larin, and M. Tkachenko, ‘Systematization of Cyber Threats in Maritime Transport’, Secur. Infocommunication Syst. Internet Things, vol. 1, no. 1, Art. no. 1, Jun. 2023, doi: 10.31861/sisiot2023.1.01008.
[20] ‘“EVER GIVEN” in the Suez Canal: when is a binding contract concluded? - Andrew Carruth | Quadrant Chambers’. Accessed: Sep. 05, 2024. [Online]. Available: https://www.quadrantchambers.com/news/ever-given-suez-canal-when-binding-contract-concluded-andrew-carruth
[21] ‘Space is booming. Here’s how to embrace the $1.8 trillion opportunity’, World Economic Forum. Accessed: Sep. 04, 2024. [Online]. Available: https://www.weforum.org/agenda/2024/04/space-economy-technology-invest-rocket-opportunity/
[22] ‘COTS Components can be Used in Small Satellites’. Accessed: Sep. 05, 2024. [Online]. Available: https://bisresearch.com/news/satellite-commercial-off-the-shelf-components-enabling-innovation-in-space-technology-
[23] S. Research, ‘Satellite Commercial-Off-the-Shelf Components Market Size, Share and Forecast to 2031’. Accessed: Sep. 05, 2024. [Online]. Available: https://straitsresearch.com/report/satellite-commercial-off-the-shelf-components-market
[24] A. Ribeiro, ‘New Deloitte report addresses increasing danger of cyber threats in space, issues call to action’, Industrial Cyber. Accessed: Sep. 05, 2024. [Online]. Available: https://industrialcyber.co/reports/new-deloitte-report-addresses-increasing-danger-of-cyber-threats-in-space-issues-call-to-action/
[25] ‘Security Threats against Space Missions’, 2015, [Online]. Available: https://public.ccsds.org/Pubs/350x1g3.pdf
[26] T. Ohmüller, ‘Improving Security of Space Link Extension (SLE) Services’, May 2008.
[27] ‘National Security Agency/Central Security Service > Cybersecurity > Quantum Key Distribution (QKD) and Quantum Cryptography QC’. Accessed: Sep. 04, 2024. [Online]. Available: https://www.nsa.gov/Cybersecurity/Quantum-Key-Distribution-QKD-and-Quantum-Cryptography-QC/
[28] ‘Eagle-1’. Accessed: Sep. 04, 2024. [Online]. Available: https://www.esa.int/Applications/Connectivity_and_Secure_Communications/Eagle-1
[29] craig miles, ‘Satellite Encryption Techniques’, Yesway Communications. Accessed: Sep. 04, 2024. [Online]. Available: https://yesway.co.uk/satellite-encryption-techniques/
[30] A. King, ‘What is an optical inter-satellite link communication terminal?’, Iridian Spectral Technologies. Accessed: Sep. 04, 2024. [Online]. Available: https://www.iridian.ca/learning_center/light-notes/what-is-an-optical-inter-satellite-link-communication-terminal/
[31] D. Werner, ‘Intersatellite optical links will shake up the ground segment. But how soon and how fast is anyone’s guess.’, SpaceNews. Accessed: Sep. 04, 2024. [Online]. Available: https://spacenews.com/intersatellite-optical-links-will-shake-up-the-ground-segment-but-how-soon-and-how-fast-is-anyones-guess/
[32] L. Bernstein, ‘Inter-Satellite Links Are Making Space Networks a Reality’. Accessed: Sep. 04, 2024. [Online]. Available: https://www.kratosdefense.com/constellations/articles/inter-satellite-links-are-making-space-networks-a-reality
[33] ‘Moonlighter, the World’s First Hacking Test Bed in Space, to Launch with Five Other Small Satellites on SpaceX CRS-28’. Accessed: Sep. 04, 2024. [Online]. Available: https://www.issnationallab.org/spx28-moonlighter-cubesat-afrl/
[34] ‘Moonlighter – HACK-A-SAT 4’. Accessed: Sep. 04, 2024. [Online]. Available: https://hackasat.com/moonlighter/
[35] ‘Space for 5G’. Accessed: Sep. 04, 2024. [Online]. Available: https://connectivity.esa.int/space-5g
[36] ‘Satellites Role in 5G: The Future of 5G | AccelerComm’. Accessed: Sep. 04, 2024. [Online]. Available: https://www.accelercomm.com/news/satellites-role-in-the-future-of-5g
[37] ‘5G Satellite Spectrum - IEEE Future Networks’. Accessed: Sep. 04, 2024. [Online]. Available: https://futurenetworks.ieee.org/topics/5g-satellite-spectrum
[38] D. Meyer, ‘Hughes combines satellite, open RAN 5G for DoD “tactical edge”’, SDxCentral. Accessed: Sep. 04, 2024. [Online]. Available: https://www.sdxcentral.com/articles/interview/hughes-combines-satellite-open-ran-5g-for-dod-tactical-edge/2024/09/
[39] A. Turner, ‘Spain’s Sateliot to launch four 5G-IoT Satellites with SpaceX in July’, Mobile Europe. Accessed: Sep. 04, 2024. [Online]. Available: https://www.mobileeurope.co.uk/spains-sateliot-to-haunch-four-5g-iot-satellites-with-spacex-in-july/
[40] E. H. last updated, ‘Elon Musk says Russia is ramping up cyberattacks on SpaceX’s Starlink systems in Ukraine’, Space.com. Accessed: Sep. 04, 2024. [Online]. Available: https://www.space.com/starlink-russian-cyberattacks-ramp-up-efforts-elon-musk
[41] I. Arghire, ‘Ransomware Gang Publishes Data Allegedly Stolen From Maritime Firm Royal Dirkzwager’, SecurityWeek. Accessed: Sep. 04, 2024. [Online]. Available: https://www.securityweek.com/ransomware-gang-publishes-data-allegedly-stolen-from-maritime-firm-royal-dirkzwager/
[42] ‘Japan’s space agency hit by series of cyberattacks since last year, official says’. Accessed: Sep. 04, 2024. [Online]. Available: https://therecord.media/japan-cyberattacks-space-agency-series
[43] ‘Aerospace Cybersecurity: Satellite Hacking (W53)’. [Online]. Available: https://pentestmag.com/course/aerospace-cybersecurity-satellite-hacking-w53/
[44] ‘Ground Control to Major Threat: Hacking the Space Link Extension Protocol’. [Online]. Available: https://visionspace.com/hacking-sle/
[45] ‘Space Link Extension (SLE) Emulation for High-Throughput Network Communication’. [Online]. Available: https://ntrs.nasa.gov/api/citations/20140017058/downloads/20140017058.pdf
[46] ‘Jamming and Cyber Attacks: How Space is Being Targeted in Ukraine’. [Online]. Available: https://www.rusi.org/explore-our-research/publications/commentary/jamming-and-cyber-attacks-how-space-being-targeted-ukraine
[47] M. Baezner and P.Robin, ‘Stuxnet’, Feb. 2018. [Online]. Available: https://www.researchgate.net/publication/323199431_Stuxnet
[48] ‘Hackers could shut down satellites — or turn them into weapons’ [Online]. Available: https://www.astronomy.com/science/hackers-could-shut-down-satellites-or-turn-them-into-weapons/
[49] Rolls-Royce, ‘Autonomous ships - The next step’ [Online]. Available: https://www.rolls-royce.com/~/media/Files/R/Rolls-Royce/documents/%20customers/marine/ship-intel/rr-ship-intel-aawa-8pg.pdf
[50] Wired ‘Inside the Cunning, Unprecedented Hack of Ukraine's Power Grid’. [Online]. Available: https://www.wired.com/2016/03/inside-cunning-unprecedented-hack-ukraines-power-grid/
Capability Overview
Cyber Resilience
About Cyber Solutions:
Aon’s Cyber Solutions offers holistic cyber risk management, unsurpassed investigative skills, and proprietary technologies to help clients uncover and quantify cyber risks, protect critical assets, and recover from cyber incidents.
General Disclaimer
This document is not intended to address any specific situation or to provide legal, regulatory, financial, or other advice. While care has been taken in the production of this document, Aon does not warrant, represent or guarantee the accuracy, adequacy, completeness or fitness for any purpose of the document or any part of it and can accept no liability for any loss incurred in any way by any person who may rely on it. Any recipient shall be responsible for the use to which it puts this document. This document has been compiled using information available to us up to its date of publication and is subject to any qualifications made in the document.
Terms of Use
The contents herein may not be reproduced, reused, reprinted or redistributed without the expressed written consent of Aon, unless otherwise authorized by Aon. To use information contained herein, please write to our team.
Our Better Being podcast series, hosted by Aon Chief Wellbeing Officer Rachel Fellowes, explores wellbeing strategies and resilience. This season we cover human sustainability, kindness in the workplace, how to measure wellbeing, managing grief and more.
Expert Views on Today's Risk Capital and Human Capital Issues
Expert Views on Today's Risk Capital and Human Capital Issues
Expert Views on Today's Risk Capital and Human Capital Issues
Better Decisions Across Interconnected Risk and People Issues.
The construction industry is under pressure from interconnected risks and notable macroeconomic developments. Learn how your organization can benefit from construction insurance and risk management.
Stay in the loop on today's most pressing cyber security matters.
Our Cyber Resilience collection gives you access to Aon’s latest insights on the evolving landscape of cyber threats and risk mitigation measures. Reach out to our experts to discuss how to make the right decisions to strengthen your organization’s cyber resilience.
Our Employee Wellbeing collection gives you access to the latest insights from Aon's human capital team. You can also reach out to the team at any time for assistance with your employee wellbeing needs.
Explore Aon's latest environmental social and governance (ESG) insights.
Our Global Insurance Market Insights highlight insurance market trends across pricing, capacity, underwriting, limits, deductibles and coverages.
How do the top risks on business leaders’ minds differ by region and how can these risks be mitigated? Explore the regional results to learn more.
Our Human Capital Analytics collection gives you access to the latest insights from Aon's human capital team. Contact us to learn how Aon’s analytics capabilities helps organizations make better workforce decisions.
Explore our hand-picked insights for human resources professionals.
Our Workforce Collection provides access to the latest insights from Aon’s Human Capital team on topics ranging from health and benefits, retirement and talent practices. You can reach out to our team at any time to learn how we can help address emerging workforce challenges.
Our Mergers and Acquisitions (M&A) collection gives you access to the latest insights from Aon's thought leaders to help dealmakers make better decisions. Explore our latest insights and reach out to the team at any time for assistance with transaction challenges and opportunities.
How do businesses navigate their way through new forms of volatility and make decisions that protect and grow their organizations?
Our Parametric Insurance Collection provides ways your organization can benefit from this simple, straightforward and fast-paying risk transfer solution. Reach out to learn how we can help you make better decisions to manage your catastrophe exposures and near-term volatility.
Our Pay Transparency and Equity collection gives you access to the latest insights from Aon's human capital team on topics ranging from pay equity to diversity, equity and inclusion. Contact us to learn how we can help your organization address these issues.
Forecasters are predicting an extremely active 2024 Atlantic hurricane season. Take measures to build resilience to mitigate risk for hurricane-prone properties.
Our Technology Collection provides access to the latest insights from Aon's thought leaders on navigating the evolving risks and opportunities of technology. Reach out to the team to learn how we can help you use technology to make better decisions for the future.
Trade, technology, weather and workforce stability are the central forces in today’s risk landscape.
Our Trade Collection gives you access to the latest insights from Aon's thought leaders on navigating the evolving risks and opportunities for international business. Reach out to our team to understand how to make better decisions around macro trends and why they matter to businesses.
With a changing climate, organizations in all sectors will need to protect their people and physical assets, reduce their carbon footprint, and invest in new solutions to thrive. Our Weather Collection provides you with critical insights to be prepared.
Our Workforce Resilience collection gives you access to the latest insights from Aon's Human Capital team. You can reach out to the team at any time for questions about how we can assess gaps and help build a more resilience workforce.