
Support

Aon's Stroz Friedberg Incident Response Services ("Stroz Friedberg") observed the use of novel malware, dubbed "Effluence," in combination with the exploit of a recent Atlassian Confluence vulnerability. Once implanted, the malware acts as a persistent backdoor and is not remediated by applying patches to Confluence. The backdoor provides capability for lateral movement to other network resources in addition to exfiltration of data from Confluence. Importantly, attackers can access the backdoor remotely without authenticating to Confluence. The malware is difficult to detect and organizations with Confluence servers are advised to investigate thoroughly, even if a patch was applied.
Stroz Friedberg was engaged to help a client perform diligence after they discovered that they had a known vulnerable (CVE-2023-22515) Atlassian Confluence Data Center server near the edge of their network. This vulnerability allows an attacker to gain unauthorized access to the administrative areas of a Confluence server.
In this specific client engagement, the cybercriminal gained initial access via the previously mentioned vulnerability and embedded a novel web shell into the Confluence server which allowed them persistent access to every web page on the server without the need for a valid user account. Typical web shells encountered with Confluence exploits are uploaded via the Confluence Plugin ability, e.g., https://github.com/dubfr33/atlassian-webshell-plugin. Such web shells are only accessible if a user has signed into Confluence or if a single webpage of the webserver has been hooked. The attacker must access the exact page of the web shell, for example, http://example.com/webshell.jsp.
The web shell encountered during Stroz Friedberg’s investigation, however, hijacks the underlying Apache Tomcat webserver and silently inserts itself between Confluence and Tomcat–making itself available on every webpage, including the unauthenticated login page. The web shell does not make any changes to the webpages and allows requests to pass through it unnoticed until a request matches specific parameters.
Stroz Friedberg identified this web shell on public malware repositories with no detections, indicating others may be at risk of this malware. Given ongoing attacks against Confluence, this post aims to raise awareness and provide initial detection methods. Public analysis of the inner workings of the malware will be published at a later date.
The web shell is split into two parts, a loader and payload. The loader acts as a normal Confluence plugin but utilizes a modified legitimate Java collections class, similar to IdentityHashMap, to hide its malicious payload. The loader is triggered via an overloaded equals() method, which decrypts the payload into a byte array containing a Java class, then loads that class via reflection—hence the raw Java class is never written to the filesystem. Once the payload is loaded, it runs a function which hides the plugin among Confluence “System Apps”, whereas a user loaded plugin would normally be among “User-Installed Apps”.
The web shell traverses internal structures of the ServletContextFactory interface in order to locate and then add itself to Tomcat’s internal applicationEventListenersList. It implements a ServletRequestListener such that any request to the Confluence server passes through the web shell first, including all pages accessible to unauthenticated users. Because the web shell is available from the login page, attackers can trigger it without needing to maintain Confluence user access. The web shell itself takes no action unless a particular query parameter is supplied. When triggered, the web shell can execute any of the following functions (which closely align with a Godzilla webshell plugin):
To assist in identifying this web shell in an environment, the below includes multiple detections for this web shell. Please take note: at this time, patching Confluence to address CVE-2023-22515 and CVE-2023-22518 will not remediate the web shell if it has been deployed.
This detection looks for plugins created in the Atlassian plugin directories. This will only identify whether a plugin was installed and not whether the plugin is malicious. To identify if a plugin was installed, look for files with a “.jar” extension in any of the following directories:
Due to the customizable nature of Confluence installations, it is prudent to check other Confluence related directories including plugin-cache and bundled-plugins.
Detecting usage of this web shell depends on review of the web server access logs. Due to the method the web shell uses, there are no obvious Indicators of Compromise (IOCs) in the web logs to detect usage of the web shell. However, one may be able to find potential usage by reviewing access to static confluence pages, such as “/login.action”, where the response size varies. For example, the following screenshot shows successful access to “/login.action” with response sizes that vary between 826 to 2574 bytes:
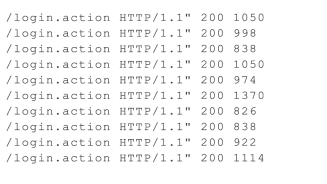
Figure 1 – Examples of malicious requests from logs located at /opt/atlassian/confluence/logs/conf_access_log.log
While we are still gathering information about this particular malware, as an early point of note – Stroz Friedberg recommends baselining your environment to find the normal range of response sizes for the environment to find the abnormal response sizes.
Detection of the web shell via this method relies on a memory capture from the server. Stroz Friedberg developed the following Yara rule which can detect the web shell in the preserved memory image:
rule ConfluencePageIndicator {
meta:
description = "Detects strings indicative of a web shell in Confluence page"
author = "Stroz Friedberg"
date = "2023-11-06"
strings:
$confluence_title = " - Confluence " ascii wide
$hide_plugin_function = "hidePlugin(" ascii wide
$system_plugin_key = "ALWAYS_SYSTEM_PLUGIN_KEYS" ascii wide
$dashes = " ----- " ascii wide
condition:
$confluence_title and $hide_plugin_function and $dashes and $system_plugin_key
}

Support
Stroz Friedberg has not thoroughly tested to what extent this novel malware is applicable to other Atlassian products. Several of the web shell functions depend on Confluence-specific APIs. However, the plugin and the loader mechanism appear to depend only on common Atlassian APIs and are potentially applicable to JIRA, BitBucket, or other Atlassian products where an attacker can install the plugin.
If you suspect you are compromised or need assistance in assessing compromise, please call our Incident Response hotline. If you are from a Law Enforcement Agency or Endpoint Detection and Response vendor and wish for more details, please contact Aon Cyber Solutions.
1 Lightweight Directory Access Protocol
While care has been taken in the preparation of this material and some of the information contained within it has been obtained from sources that Stroz Friedberg believes to be reliable (including third-party sources), Stroz Friedberg does not warrant, represent, or guarantee the accuracy, adequacy, completeness or fitness for any purpose of the article and accepts no liability for any loss incurred in any way whatsoever by any person or organization who may rely upon it. It is for informational purposes only. You should consult with your own professional advisors or IT specialists before implementing any recommendation or following the guidance provided herein. Further, we endeavor to provide accurate and timely information, there can be no guarantee that such information is accurate as of the date it is received or that it will continue to be accurate in the future. Further, this article has been compiled using information available to us up to 11/8/23.

Support
About Cyber Solutions:
Aon’s Cyber Solutions offers holistic cyber risk management, unsurpassed investigative skills, and proprietary technologies to help clients uncover and quantify cyber risks, protect critical assets, and recover from cyber incidents.
General Disclaimer
This document is not intended to address any specific situation or to provide legal, regulatory, financial, or other advice. While care has been taken in the production of this document, Aon does not warrant, represent or guarantee the accuracy, adequacy, completeness or fitness for any purpose of the document or any part of it and can accept no liability for any loss incurred in any way by any person who may rely on it. Any recipient shall be responsible for the use to which it puts this document. This document has been compiled using information available to us up to its date of publication and is subject to any qualifications made in the document.
Terms of Use
The contents herein may not be reproduced, reused, reprinted or redistributed without the expressed written consent of Aon, unless otherwise authorized by Aon. To use information contained herein, please write to our team.
Our Better Being podcast series, hosted by Aon Chief Wellbeing Officer Rachel Fellowes, explores wellbeing strategies and resilience. This season we cover human sustainability, kindness in the workplace, how to measure wellbeing, managing grief and more.
Expert Views on Today's Risk Capital and Human Capital Issues
Expert Views on Today's Risk Capital and Human Capital Issues
Expert Views on Today's Risk Capital and Human Capital Issues
The construction industry is under pressure from interconnected risks and notable macroeconomic developments. Learn how your organization can benefit from construction insurance and risk management.
Stay in the loop on today's most pressing cyber security matters.
Our Cyber Resilience collection gives you access to Aon’s latest insights on the evolving landscape of cyber threats and risk mitigation measures. Reach out to our experts to discuss how to make the right decisions to strengthen your organization’s cyber resilience.
Our Employee Wellbeing collection gives you access to the latest insights from Aon's human capital team. You can also reach out to the team at any time for assistance with your employee wellbeing needs.
Explore Aon's latest environmental social and governance (ESG) insights.
Our Global Insurance Market Insights highlight insurance market trends across pricing, capacity, underwriting, limits, deductibles and coverages.
How do the top risks on business leaders’ minds differ by region and how can these risks be mitigated? Explore the regional results to learn more.
Our Human Capital Analytics collection gives you access to the latest insights from Aon's human capital team. Contact us to learn how Aon’s analytics capabilities helps organizations make better workforce decisions.
Explore our hand-picked insights for human resources professionals.
Our Workforce Collection provides access to the latest insights from Aon’s Human Capital team on topics ranging from health and benefits, retirement and talent practices. You can reach out to our team at any time to learn how we can help address emerging workforce challenges.
Our Mergers and Acquisitions (M&A) collection gives you access to the latest insights from Aon's thought leaders to help dealmakers make better decisions. Explore our latest insights and reach out to the team at any time for assistance with transaction challenges and opportunities.
How do businesses navigate their way through new forms of volatility and make decisions that protect and grow their organizations?
Our Parametric Insurance Collection provides ways your organization can benefit from this simple, straightforward and fast-paying risk transfer solution. Reach out to learn how we can help you make better decisions to manage your catastrophe exposures and near-term volatility.
Our Pay Transparency and Equity collection gives you access to the latest insights from Aon's human capital team on topics ranging from pay equity to diversity, equity and inclusion. Contact us to learn how we can help your organization address these issues.
Forecasters are predicting an extremely active 2024 Atlantic hurricane season. Take measures to build resilience to mitigate risk for hurricane-prone properties.
Our Technology Collection provides access to the latest insights from Aon's thought leaders on navigating the evolving risks and opportunities of technology. Reach out to the team to learn how we can help you use technology to make better decisions for the future.
Trade, technology, weather and workforce stability are the central forces in today’s risk landscape.
Our Trade Collection gives you access to the latest insights from Aon's thought leaders on navigating the evolving risks and opportunities for international business. Reach out to our team to understand how to make better decisions around macro trends and why they matter to businesses.
With a changing climate, organizations in all sectors will need to protect their people and physical assets, reduce their carbon footprint, and invest in new solutions to thrive. Our Weather Collection provides you with critical insights to be prepared.
Our Workforce Resilience collection gives you access to the latest insights from Aon's Human Capital team. You can reach out to the team at any time for questions about how we can assess gaps and help build a more resilience workforce.

Article 4 mins
Organizations can demonstrate their commitment to global sustainability and a low-carbon future by addressing verification challenges and adopting best practices.

Report 13 mins
Engaging a changing workforce requires data and innovation. Workers increasingly expect more than just a paycheck. In response, organizations are balancing costs with the ability to provide a compelling employee experience.

Article 15 mins
Market stability prevails in management liability lines as insurers continue to seek market share. However, expanding technologies, increased litigation and macroeconomic factors are causing growing uncertainty and underwriting concerns.

Article 7 mins
There is an opportunity to develop a strategy around financial education in the workplace. Globally, our latest data finds 11 percent of employees receive financial education from their employer, but 37 percent expect it. How can employers bridge this gap?

Article 12 mins
The UK insurance market has seen increased competition and softening conditions. Insurers have capitalized on strong financials and capacity, benefiting buyers. Yet, challenges in specific areas have required strategic engagement and robust risk management for optimal outcomes.

Article 12 mins
With growing global regulations and rising stakeholder and talent expectations, pay equity has shifted from a mere HR initiative to a top C-suite priority that goes beyond compliance.

Article 7 mins
A well-structured open enrollment process is one that leverages innovative technology, encourages cost-effective use of healthcare resources and reduces unnecessary spending — benefiting both employees and employers.

Article 19 mins
While there have been significant strides toward a more inclusive workforce, the gender pay gap persists. Discover how organizations can continue to make progress with interconnected policies and comprehensive programs that support an inclusive environment at every career and life stage.

Article 15 mins
After a period of significant volatility, a more optimistic outlook is on the horizon for the life sciences industry in 2025. With the right level of preparedness, firms can take full advantage of the potential opportunities the new year will bring.

Article 6 mins
Decarbonizing construction demands new materials and approaches, with a focus on managing risk and securing capital. By aligning sustainability with business strategy and risk management, the industry can meet net-zero targets.

Article 8 mins
Nearly 20 million people get cancer each year,<sup>1</sup> and the impact is far-reaching — from those diagnosed to their loved ones and colleagues. When developing a meaningful cancer prevention strategy, employers must show empathy and compassion while managing rising costs.

Alert 14 mins
In the face of the L.A. wildfires, impacted businesses’ top priority is their people. A three-phased approach can help build business resilience and mitigate the effects of future events.

Article 23 mins
Rapid growth in data center construction, spurred by AI advancements and cloud demand, creates interconnected risks for developers. However, with effective risk management solutions, navigating this dynamic market while prioritizing sustainability is possible.

Article 8 mins
In an industry with tight operating margins, FAB organizations face significant challenges in managing spend and protecting their financial health — requiring industry leaders to adopt a sophisticated approach to risk capital optimization.

Article 15 mins
The risk capital landscape is poised for change, driven by emerging trends reshaping market dynamics. With a buyer-friendly market currently prevailing across most lines, opportunities abound for strategic investment and risk management.

Article 9 mins
When a workers compensation claim goes to litigation, expenses rise dramatically — a burden that is often shouldered by the business. To mitigate attorney-related costs, organizations should re-think their approach to engaging injured workers and use artificial intelligence to enhance outcomes.

Article 35 mins
Human resources is increasingly involved in all areas of a company’s strategy. As the workforce changes, HR leaders should identify and leverage these five important and evolving trends.

Article 6 mins
Long-term care is expensive, and costs are rising due to shortages. With the population aging at the fastest rate in a century, finding solutions to pay for care is an urgent priority. How can employers support this growing population?

Article 7 mins
With a multi-generational and diverse workforce, it is important for employers to develop benefit communications and engagement strategies to help employees understand their unique benefit options. Here are five useful tips to consider.

Article 13 mins
Rising medical costs are a global phenomenon. Aon’s 2025 Global Medical Trend Rate Survey found that costs are projected to rise 10 percent in 2025.

Article 7 mins
As healthcare costs continue to rise, employers are trying to balance the need to take care of their workers with the need to keep costs under control. Aon’s 2025 U.S. Health Survey provides insights into the choices employers are making, and their potential effects on costs.

Article 9 mins
Pension reforms in Europe are reshaping retirement planning, demanding more oversight from employers and new strategies for employees’ financial wellbeing.

Article 6 mins
Non-financial risks are often difficult to predict and quantify, yet present a real threat to financial institutions. In this volatile environment, risk management is playing a greater role in creating business resilience and identifying where capital should be deployed.

Article 9 mins
Daniel Halter, Director Global Insurance at Sandoz, discusses how smart risk and insurance management supported the Sandoz core mission to provide affordable, off-patent medicines to patients who need them most with Ana Serdarevic, Head of Aon’s Transaction Advisory Services for DACH.

Article 7 mins
Business leaders are aware of AI-driven cyber risks and their implications. But understanding changing risk profiles to make better decisions around the management of new exposures is the key to cyber resilience.

Article 9 mins
U.S. freight and commuter rail industries are facing excess liability and property issues for different reasons. These railroads are critical to infrastructure and vital to the economy, yet finding effective solutions remains complex.

Article 11 mins
As private companies prepare for an IPO, they face increased risks that require directors and key leaders to adopt essential risk management strategies to ensure a smooth transition.

Article 10 mins
As climate change intensifies the frequency and severity of extreme weather events, public entities and businesses need more flexible funding solutions. Parametric stands out as an adaptable resource capable of swiftly responding to potential disasters.

Article 17 mins
Funding challenges due to macroeconomic factors have prevented several green and blue hydrogen projects from getting off the ground. Organizations facing hurdles in accessing capital can work with risk and insurance experts to expedite projects and help make the promise of hydrogen a reality.

Article 11 mins
Learn how strong human capital strategies can help recruit, retain and motivate vital talent in a competitive and evolving job market.

Article 7 mins
As corporate boards meet to discuss strategy, including any changes to executive compensation, there are key trends to consider for the year ahead.

Article 6 mins
Companies aiming to be a net-zero company may face many challenges during the biofuels transition. Read more on risk strategies to cut through complexity.

Article 6 mins
With DC schemes growing across Europe, many organizations are realizing the importance of ensuring strong performance from their investments. Here’s how asset owners and managers can optimize DC outcomes through the right investment strategy.

Article 9 mins
With no federal paid leave law in the U.S., employers have limited guidance in designing equitable and comprehensive paid leave programs to support their workforce. Looking beyond compliance to focus on strategy and values will help create fair and well-designed policies.

Article 8 mins
Risk managers are increasingly looking to Alternative Risk Transfer Solutions for potential enhancements in managing risk.

Article 8 mins
Amid economic uncertainty, companies are taking a careful approach to hiring and salary planning — one that includes focused hiring strategies, revising salary budgets and implementing measures that respond to the current economic environment.

Alert 7 mins
The current operating environment in the Middle East is increasingly complex and multifaceted, characterized by ongoing conflicts in Gaza, Israel, Lebanon and neighboring states, alongside significant changes in the business and insurance environment.

Article 8 mins
Hurricanes Helene and Milton insured loss estimates are expected to fall between $34 billion and $54 billion. Healthy, well-capitalized insurance and reinsurance markets are positioned to absorb those losses.

Article 17 mins
Buyer-friendly conditions continued across much of the global insurance market in Q3, painting a largely positive picture as we head into year-end renewals.

Article 10 mins
A successful M&A strategy relies on due diligence across financial, legal, human capital, technology, cyber security and intellectual property risks. As cyber threats become more complex, robust cyber due diligence in private equity and acquisitions is increasingly necessary.

Article 8 mins
Cargo theft in the transportation industry is escalating, driven by sophisticated criminal tactics that exploit both physical and digital vulnerabilities. Businesses must adopt proactive risk management strategies to counter these evolving threats.

Article 11 mins
Trade, technology, weather and the workforce are interconnected trends shaping the future of business in North America. Understanding them is key to long-term resilience.

Article 9 mins
Competition and capacity are dominating the cyber liability market and pricing remains favorable as a result. Taking advantage of the current buyer’s market to build sustained cyber resilience is the key to success.

Article 10 mins
The growing renewable energy sector is boosting M&A activity. Risk transfer solutions can help unlock capital access in these transactions.

Article 7 mins
Digitalization presents both opportunities and challenges in life sciences, driving new organizational approaches to human capital to keep up with evolving talent needs while building a resilient workforce.

Article 5 mins
As financial institutions reshape human capital strategies for the digital age, leaders face pressure to balance the risks and opportunities of digitalization.

Article 9 mins
Employers are concerned that previous wellbeing strategies aren’t moving the needle enough. But when wellbeing is part of an organization’s culture, it has positive effects on costs, engagement and productivity.

Article 6 mins
Financial institutions can increase their resilience to volatile threats through enhanced risk management frameworks and innovative models powered by people data and technology.

Article 10 mins
As the deadline for implementing the EU Pay Transparency Directive fast approaches, some financial institutions feel unprepared to comply. These five steps can help guide the way through the upcoming regulatory landscape.

Article 9 mins
Thriving organizations rely on thriving employees to succeed. With healthcare costs on the rise, it’s time for employers to challenge the status quo in providing health benefits. Organizations need to consider the human side of these increases and take bold action to achieve better outcomes.

Article 9 mins
The aviation industry is watching the rise in nuclear verdicts with concern as social inflation and associated risks continue to squeeze the sector. Organizations should review their risk management processes to limit the dollar value of future losses.

Article 12 mins
As AI evolves, directors and officers must maneuver through a complex landscape of regulatory and legal risks. Implementing best practices around the use of AI and robust governance-focused risk mitigation can help manage exposures.

Article 11 mins
Middle market organizations face unique challenges in the ever-changing cyber environment, requiring holistic insurance solutions and enhanced resilience readiness to manage risks that could impact profitability.

Article 17 mins
With life expectancies and retirement ages on the rise, organizations can capitalize on the value that older employees offer and support them by fostering a workplace where both the business and its people thrive.

Article 8 mins
As climate change compounds wildfire risk, organizations play a critical role in protecting their workforce before and after an event.

Article 10 mins
The transportation and logistics industry faces unique challenges which can negatively impact employees' health. A cultural shift to more tailored wellbeing strategies can improve health outcomes and boost company performance.

Article 8 mins
As workforce and skills shortages emerge as a significant future risk, companies seek winning talent and tech solutions.

Article 6 mins
Pooled employer plans (PEPs) can offer a streamlined solution to the retirement planning challenges inherent in spin-off and M&A events.

Article 20 mins
The role of HR professionals is becoming more strategic, which requires collaboration with other areas of an organization to help drive growth. Given that people and benefit costs are a large portion of business expenses, partnering with finance is a natural step forward.

Article 5 mins
Aon analyzes employee perception about return to office policies following the COVID-19 pandemic, as well as recent actions one organization took for alleged lack of remote employee productivity.

Article 11 mins
Despite subdued global M&A in 2023, positive trends have been emerging in the M&A insurance market to help clients improve their deal-making and ‘value-protection on investment’.

Article 7 mins
Graeme Hudson and Ghonche Alavi from Crisis24 discuss Crisis24’s approach to Political Evacuation and Threat Management with Cara LaTorre from the Financial Services Group at Aon.

Article 8 mins
European construction contractors are looking with increasing interest at Asia, but to expand successfully into the region, they need to overcome key workforce and market challenges.

Article 8 mins
As digitalization presents new risks and opportunities for life sciences organizations, implementing cyber and data resilience ensures that innovation doesn’t result in business interruption.

Article 7 mins
For insurers, making decisions on where and how to deploy capital becomes more difficult during times of volatility.

Article 5 mins
Employers in the U.S. should understand the unique risks associated with voluntary benefit captives when considering alternative insurance arrangements for their voluntary benefit plans.

Article 7 mins
Workers compensation is an area of risk management that could benefit from a more holistic approach. A safety program that incorporates wellbeing and uses data in a meaningful way can contribute greatly to lowering costs.

Article 8 mins
Firefighters face a unique set of risks and long-term health consequences from their jobs. Aon worked with Minnesota firefighters to create a benefit program to address three primary health issues.

Article 8 mins
Open legacy workers compensation claims place rising financial burdens on employers, who are faced with closing out aged claim inventory and improving their balance sheets in the process.

Article 5 mins
Organizations must consider the impact of climate change on property, which will vary now and years into the future. Therefore, a thoughtful approach can enhance risk mitigation and resilience strategies.

Article 8 mins
Helping midsize organizations strike the right balance between risk and compliance with a comprehensive regulatory and compliance framework.

Article 5 mins
As U.S. employers balance costs with providing employees more value from their benefits, creating an annual healthcare enrollment process that includes more choice and guidance can accomplish both goals.

Article 10 mins
With many insurers reporting healthy profits in 2023, and in response to notable improvements in the reinsurance market, the insurance market in Q2 2024 remained growth-oriented.

Alert 3 mins
On July 19, 2024, the CrowdStrike outage became one of the largest IT events in history, impacting businesses and customers around the world. Leaders now have an opportunity to reexamine technology dependencies and business continuity plans to mitigate similar risks in future.

Article 6 mins
Insurers are some of the world’s largest institutional investors. Recognising their crucial role in driving the global climate transition, they should identify and analyse climate-related risks and opportunities to improve long-term risk-adjusted returns.

Article 7 mins
The global CrowdStrike IT outage demonstrated that even non-malicious cyber incidents may have serious repercussions. Events like these serve as a wake-up call for businesses to review their cyber resilience and be prepared for more significant incidents in the future.

Article 4 mins
More global benefits professionals are aligning benefit strategy to an employer’s identity and values.

Alert 10 mins
CrowdStrike, a global cybersecurity firm, released an update for its Falcon sensor, which caused system crashes on Microsoft Windows systems globally.

Article 8 mins
Cyber incidents continue to grow in frequency and severity, especially as new technology emerges. While D&O and cyber liability policies offer distinct coverage differences, terms need to be carefully structured to avoid potential gaps.

Article 6 mins
Insurers are venturing into the thriving digital landscape of the Metaverse, covering virtual assets, safeguarding intellectual property, and protecting the wellbeing of users and avatars. With this evolution, comes new challenges and the unique opportunity to shape the future of insurance.

Article 10 mins
Record-warm Atlantic Ocean temperatures and a shift to La Niña conditions have led forecasters to predict an extremely active Atlantic hurricane season in 2024. Learn how to build business resilience to mitigate risk for hurricane-prone properties.

Alert 7 mins
The U.S. Supreme Court has changed the way laws are interpreted in the development of regulations. This change has the potential for far-reaching consequences for both regulatory agencies and employers.

Article 18 mins
For institutional investors, engaging an outsourced chief investment officer, or OCIO, is one of the most critical decisions an organization can make. Choosing the right partner can lead to achieving the desired results or unexpected consequences.

Article 4 mins
Overview of the current trade credit insurance market and outlook on trend developments.

Article 11 mins
The need to attract and retain high-quality talent in an environment of intense competition is at the forefront of professional services leaders’ minds.

Article 11 mins
Renewable energy is critical to meet net-zero targets, but as the industry grows, so do cyber attack surfaces. Learn how to prepare for emerging threats and support long-term ambitions.

Article 7 mins
As the scale and speed of interconnected risks escalate, innovative risk management strategies help FAB businesses build the resilience and agility needed to thrive.

Article 10 mins
The renewable energy sector is undergoing a sweeping transformation, as it plays a pivotal role in the challenge to achieve global net-zero goals. Attracting, upskilling and retaining talent is critical for sustainability.

Article 7 mins
Contractors in EMEA face an array of risks they must mitigate or transfer while managing the complexities inherent in major construction projects.
Article 12 mins
As more companies seek to reduce their carbon footprint, the renewable energy sector continues to grow, presenting both opportunities and red flags for organizations with renewable energy growth plans.

Article 6 mins
Proactive risk management and data-driven reshoring strategies can empower risk managers in logistics companies to navigate supply chain complexities with confidence.

Article 5 mins
As more companies become comfortable using captives and understanding the value they add, captives are likely to become further embedded into corporate risk strategies, regardless of market conditions.

Article 7 mins
Helping midsize organizations leverage key partnerships to address challenges around talent, market, regulatory compliance, and leveraging capital.

Article 12 mins
A rapid rise in medical plan costs is being driven in part by high-cost claimants — a high-risk group that disproportionately accounts for a large amount of healthcare costs. Here are strategies for addressing this issue.

Article 9 mins
Online benefits platforms are a key component of the overall employee value proposition. As employers maximize the ROI of their people spend, here are four tips which may assist with implementing a successful online benefits platform.

Article 8 mins
Efforts to bring more transparency to pay practices shine a light on benefits equity — and it’s not only about wages and salary.

Article 3 mins
The rapid pace of digitalisation means that organisations in the UK are constantly struggling with the ever-present threat of cyber attacks.

Article 2 mins
Equity has an important part to play in a balanced strategy to improve the attraction and retention of key employees.

Article 2 mins
How are business leaders adapting to a generational change in how work gets done?

Article 2 mins
Lori Goltermann, CEO of Regions and Enterprise Clients, Aon examines the main issues discussed at the event.

Article 2 mins
Our panel discussion looked at the issues facing corporate treasurers and how they have become more complex and interconnected.

Article 3 mins
Businesses are still in search of competition, alternatives and innovation in their insurance programmes.

Article 2 mins
Companies and financial sponsors are constantly seeking innovative and capital-efficient ways to facilitate M&A deals.

Article 2 mins
Professor Trevor Williams analyses the latest indicators and what they mean for the UK — and global — economy.

Article 2 mins
How Aon is moving further, faster to bring new, innovative solutions that address companies’ risk and people challenges.

Article 5 mins
Today's employers need to continually learn and adapt to emerging technologies and skills if they are to thrive in the talent landscape.

Article 3 mins
Companies that operate around the world need to have a global appreciation of the heightening geopolitical risk.

Article 6 mins
Collective retirement plans are growing in popularity and improving employees’ financial wellbeing in the process. Other advantages that haven’t been as widely explored include how these retirement structures allow HR to shift its focus to strategy.

Article 8 mins
Getting ahead of risk is vital for North American construction contractors, as they aim to manage evolving issues, while delivering job safety, solving workforce shortages and containing project costs.

Alert 6 mins
The Department of Labor released a final rule increasing overtime protections for the standard salary level threshold for the “white collar" exemptions and the threshold for employees classified as Highly Compensated Employees. Employers need to prepare for these significant changes.

Article 10 mins
Climate change adaptation and the transition to net zero present huge premium growth opportunities for insurers. The key question is how to get started.

Article 7 mins
As the cyber insurance landscape continues to evolve in EMEA, companies need actionable insights and solutions to strengthen their cyber risk strategies.

Article 9 mins
The challenges of 2023 eroded the buffers that many insurers had previously enjoyed, bringing an increased focus on capital management and a variety of capital sources according to Aon’s capital poll.

Article 6 mins
As healthcare costs rise, voluntary benefits are a critical component of engaging employees, while also helping to manage direct and indirect medical expenses. Here are three strategies for employers to make the most of their voluntary benefits.

Article 8 mins
The expansive scope, stringent sanctions and pivotal role of management related to the new NIS2 Directive provide a strong foundation to protect against evolving cyber risks.

Article 8 mins
The London insurance market seeks a generation of game-changers who can navigate uncertainties and drive innovation to ensure the industry’s future success in a digitalised world.

Article 3 mins
From global supply chain risks to climate insecurity, organizations face challenges and complexities on a scale rarely seen before.

Article 16 mins
Artificial intelligence is having a measurable impact across all aspects of HR — from talent management to compensation, health and benefits, and retirement planning. To effectively harness the technology, HR leaders must ensure both their own teams and the wider workforce are prepared.

Article 3 mins
Risk Capital CEO Andy Marcell and Human Capital CEO Lambros Lambrou discuss how innovations in Risk Capital and Human Capital can help organizations boost resilience and navigate volatility.

Case Study 3 mins
Aon partnered with UK financial advice firm M&G Wealth to help the firm better understand the make-up of a highly successful advisor of the future, including the skills needed given shifts in societal needs, technology and regulation.

Article 8 mins
Advanced analytics can empower organizations with deeper insights into the risks and opportunities surrounding renewables, while also supporting energy transition investment.

Article 17 mins
Positive performance in 2023 fueled insurer growth ambitions but underwriting remained disciplined in the first quarter of 2024.

Article 12 mins
While digitalization is delivering transformational change to R&D across the sector, it is also rapidly reshaping recruitment and retention strategies.

Alert 6 mins
The FTC has announced a rule that bans noncompetes and clauses that have a similar effect. While the rule will face legal challenges, employers should take steps now to prepare for an environment where they cannot use noncompete agreements.

Article 7 mins
Risk advisory services can help construction stakeholders navigate uncertainties, optimize performance and drive growth in their projects.
Article 9 mins
While there are similarities in the risk profile of floating offshore wind and bottom-fixed offshore wind, challenges like unproven technology and tow-to-port strategies for maintenance require a collaborative approach between owners/developers and their insurance partners.

Article 4 mins
Macrotrends are transforming our world and creating emerging property-casualty exposures, which will have profound implications for the insurance industry.

Article 7 mins
Understanding market trends and future projections in an evolving cyber insurance market is paramount to strengthening risk mitigation and transfer strategies.

Article 5 mins
In an era of escalating climate-related challenges, the construction industry is turning to advanced climate modeling to fortify its risk management strategies.

Article 14 mins
Advances in technology will not only transform healthcare and treatment outcomes — benefit offerings, access to care, diagnosis, treatment and affordability challenges will also be radically changed. Here is what to expect as these efforts take shape globally.

Article 10 mins
As healthcare costs continue to rise, employers are struggling to balance cost control with attracting and retaining talent. The results of Aon's 2024 U.S. Health Survey point to key strategies organizations are using to help.

Article 11 mins
As the world races to reduce climate risks and limit CO<sub>2</sub> emissions, the demand for scalable and cost-effective decarbonization technologies is increasing. Carbon capture projects form an important part of the low carbon energy transition, bringing both challenges and opportunities.

Article 7 mins
Growing extreme heat conditions have escalated risks, delays and costs for the construction industry in North America. Parametric insurance can help protect against such risks, offering contractors and building owners agility, efficiency and flexibility.

Article 9 mins
The launch of the Unified Patent Court allows for a new patent filing process across Europe using a centralized system. While this brings significant financial and operational benefits, navigating these changes will demand a robust litigation risk management strategy.

Article 8 mins
Construction projects in EMEA are often impacted by extreme heat, leading to project delays and increased costs. Many heat exposures are excluded by traditional markets, however, parametric is a flexible solution that can help mitigate these risks.

Article 12 mins
New regulations in the U.S. and Europe will require companies to be more transparent about their pay practices. Combined with willingness among workers to talk about salary, the era of pay transparency is here.

Article 11 mins
As companies tailor their health and benefits to meet the needs of their employees, vital areas for support include family building and menopause.

Article 7 mins
Complex market dynamics in the construction industry are pushing organizations to proactively explore alternative risk transfer solutions, including parametric insurance and captives.

Article 11 mins
As new job roles and technologies emerge in the natural resources industry, employee expectations are also shifting. Leaders must rise to the challenge of securing talent to meet the world’s future energy needs.

Article 5 mins
Rulemaking from the Securities and Exchange Commission (SEC) highlights the importance of company transparency with investors and regulators around risk management and the impact of cyber events.

Article 13 mins
Five ways financial institutions can balance investment with prudence in an uncertain economic climate.

Article 12 mins
An increasingly interconnected and complex risk landscape continues to shape risk strategies and market responses.

Article 13 mins
To be successful, business leaders must keep pace with the key trends that will impact the risk and insurance landscape in 2024.

Article 9 mins
Taking a new approach to talent management and planning for worker shortages can help businesses in the energy and power industries build greater operational resilience.

Article 8 mins
As organizations build diversity, equity, inclusion and belonging in the workplace, they must also ensure benefit plans are designed and customized to meet the needs of a diverse workforce.

Article 11 mins
For investors, climate change means navigating uncertainties and understanding a wide range of potential outcomes.

Article 8 mins
Extreme cold and freeze were responsible for $15 billion worth of structural damage in recent years, as well as business interruption and supply chain impacts. We explore the threat chronic hazards pose and consider the influence of climate change on business.

Article 7 mins
The global D&O market remains soft, creating a favorable environment for buyers. With abundant capacity and increased competition, capitalizing on conditions now is critical as rates are showing signs of moderating.

Article 17 mins
It's never been more important for HR leaders to help shape and support the execution of business strategies. However, to be successful in today’s volatile world, HR teams must stand ready to understand and harness five fast moving trends.

Article 9 mins
Supply chain disruptions can have serious reputational repercussions, causing plummeting shareholder value and diminished stakeholder trust. The potential fallout underscores the need for management strategies that collectively address these risks.

Article 13 mins
To feed a growing global population, FAB organizations must build operational resilience to overcome supply chain, cyber, geopolitical and climate risks.

Article 10 mins
Businesses considering pension risk transfer to mitigate volatility should prepare now to be well-positioned for market opportunities.

Article 7 mins
Improving retirement plan governance is crucial during economic uncertainty. Collective retirement plans, like a pooled employer plan, reduce risk and streamline administrative expenses for employers while also boosting employee support.

Article 4 mins
Senior executives aren’t letting a tough market for transactions stop them from finding new approaches to closing deals.

Article 7 mins
To stay competitive, middle-market companies need to navigate the current economic volatility and invest in their technology and talent.

Article 7 mins
Host and chief marketing officer, Reinsurance Solutions, Alexandra Lewis, is joined by UK Investment Partner at Aon, Jennifer O’Neill, for insights into the critical role that biodiversity plays in planning for the future.

Article 6 mins
Organizations faced complex challenges in risk capital and human capital throughout 2023, prompting leaders to turn to new ways of doing business.

Article 8 mins
Good agricultural practices reduce emissions, expand carbon sequestration and benefit the supply chain from the very first mile — all key components of achieving future climate goals.

Article 6 mins
In today’s increasingly volatile global economy, business leaders are focusing on two key areas of decision making: risk capital and human capital.

Article 6 mins
Our Fashion and Luxury Goods EMEA Insurance Market Insights Report discusses the macro events that impacted the insurance market in the fourth quarter of 2023 in the Fashion and Luxury Goods Industry in EMEA.

Article 3 mins
Hear from Aon and industry thought leaders to increase your working knowledge of Parametric Solutions through our four-part educational video series.

Article 7 mins
By taking a 360<sup>o </sup>view of employee wellbeing, leaders can build the resilience of their organizations while improving workplace experiences.

Article 4 mins
Financial institutions are falling short on providing organizational structure, building future skills and creating value within their organization. Addressing these is critical to future success.

Article 5 mins
With technology advancements, new consumer expectations and unpredictable markets, retailers face hurdles in building a resilient workforce. Here are two actions to take for a stronger future.

Article 6 mins
Parametric solutions have the flexibility to make hard-to-predict and often uninsurable “grey swan” events insurable. Such is the case for earthquakes — a potentially catastrophic risk across the globe.

Article 9 mins
The insurance industry can help the economy transition to alternative energy sources and mitigate the impacts of climate change — from facilitating capital for clean technologies to protecting people and businesses.

Article 7 mins
Technological innovations offer business leaders many opportunities to improve the cost and efficacy of employee health and benefits plans.

Article 7 mins
The non-standardized nature of cyber and E&O policy wording creates the opportunity to mold an individually tailored and responsive risk transfer tool.

Article 8 mins
With medical costs on the rise, companies are looking for ways to avoid passing the increased financial burden onto employees.

Article 5 mins
As data becomes more advanced and precise, so does parametric insurance as a risk solution — a win-win for both risk managers and insurers.

Article 5 mins
Ensuring future operational resilience of an acquired TMC business during an M&A starts with getting cyber due diligence right.

Article 6 mins
Often overlooked, intellectual property is an asset in the Technology, Media & Communications industry that must have effective risk management to support an organization’s overall operational resilience strategy.

Article 7 mins
The landscape for U.S. and UK pension plans has changed greatly. Companies are mitigating risks to meet regulatory requirements and protect their employees and finances.

Article 7 mins
Our research shows three workforce challenges specific to technology companies. We highlight ways to close these gaps — which is key to future industry success.

Article 6 mins
As hiring and employee turnover slows down, employers have an opportunity to rethink their salary increase strategy for 2024.

Article 7 mins
Web 3.0 is coming. Every luxury goods business can profit from the use of its related technologies in digital assets, such as NFTs and the metaverse, but cyber security must keep pace.

Article 5 mins
Funding to grow and innovate in the fashion and luxury goods industry can come from both traditional and non-traditional sources — like M&A and leveraging a brand’s intellectual property.

Article 5 mins
With more brands looking to reposition themselves in the fashion and luxury industry and secure their future, a robust workforce resilience strategy will be key.

Article 8 mins
Navigating complex, large mergers and acquisitions is a rare challenge for risk managers in life sciences. In these high-stakes scenarios, a reassessment of risk profiles and a strategic overhaul of risk financing becomes imperative to ensure the effectiveness of deals.

Article 7 mins
In a landscape where IP is increasingly becoming integral to company valuations, many business leaders, boards, patent attorneys and litigation teams are making IP insurance a key asset in their toolkits.

Article 11 mins
Construction and Real Estate industry respondents to our Global Risk Management Survey (GRMS) ranked economic slowdown or slow recovery and failure to attract or retain top talent as their two most critical risks.

Article 10 mins
Financial Institutions respondents to our Global Risk Management Survey (GRMS) ranked cyber attack or data breach and regulatory or legislative changes as their two most critical risks.

Article 12 mins
Financial Sponsors respondents to our Global Risk Management Survey (GRMS) ranked cash flow or liquidity risk and capital availability as their two most critical risks.

Article 13 mins
Food, agribusiness and beverage industry respondents to our Global Risk Management Survey (GRMS) ranked commodity price risk or scarcity of materials and supply chain or distribution failure as their two most critical risks.

Article 9 mins
Healthcare respondents to our Global Risk Management Survey (GRMS) ranked cyber attack or data breach and workforce shortage as their two most critical risks.

Article 8 mins
Hospitality, Travel and Leisure industry respondents to our Global Risk Management Survey (GRMS) ranked cyber attack or data breach and economic slowdown or slow recovery as their two most critical risks.

Article 10 mins
Industrials and Manufacturing respondents to our Global Risk Management Survey (GRMS) ranked commodity price risk or scarcity of materials and supply chain or distribution failure as their two most critical risks.

Article 11 mins
Insurance industry respondents to our Global Risk Management Survey (GRMS) ranked cyber attack or data breach and failure to attract or retain top talent as their two most critical risks.

Article 11 mins
Life Sciences industry respondents to our Global Risk Management Survey (GRMS) ranked supply chain or distribution failure and cyber attack or data breach as their two most critical risks.

Article 11 mins
Natural Resources industry respondents to our Global Risk Management Survey (GRMS) ranked business interruption and regulatory or legislative changes as their two most critical risks.

Article 9 mins
Professional Service respondents to our Global Risk Management Survey (GRMS) ranked cyber attack or data breach and failure to attract or retain top talent as their two most critical risks.

Article 11 mins
Public Sector respondents to our Global Risk Management Survey (GRMS) ranked cyber attack or data breach and damage to brand or reputation as their two most critical risks.

Article 13 mins
Retail and Consumer Goods respondents to our Global Risk Management Survey (GRMS) ranked cyber attack or data breach and supply chain or distribution failure as their two most critical risks.

Article 13 mins
Sports and Entertainment industry respondents to our Global Risk Management Survey (GRMS) ranked damage to brand or reputation and business interruption as their two most critical risks.

Article 12 mins
Technology, Media and Communications industry respondents to our Global Risk Management Survey (GRMS) ranked cyber attack or data breach and failure to attract or retain top talent as their two most critical risks.

Article 9 mins
Transportation and logistics industry respondents to our Global Risk Management Survey (GRMS) ranked cyber attack or data breach and economic slowdown or slow recovery as their two most critical risks.

Article 6 mins
Data and Governance have an important role in managing reputational risk and preventing supply chain issues in the Fashion and Luxury Goods Industry.

Article 8 mins
As ESG scrutiny intensifies, luxury goods brands will need to juggle competing stakeholder demands.

Article 12 mins
Asia Pacific respondents to our Global Risk Management Survey (GRMS) ranked cyber attack or data breach as the number one current and future risk for the region.

Article 10 mins
European respondents to our Global Risk Management Survey (GRMS) ranked cyber attack or data breach as the number one current and future risk for the region.

Article 8 mins
Latin American respondents to our Global Risk Management Survey (GRMS) ranked business interruption as the number one current risk for the region.

Article 12 mins
North American respondents to our Global Risk Management Survey (GRMS) ranked cyber attack or data breach as the number one current and future risk for the region.

Article 8 mins
Middle East and Africa respondents to our Global Risk Management Survey (GRMS) ranked economic slowdown or slow recovery as the number one current and future risk for the region.

Article 9 mins
UK respondents to our Global Risk Management Survey (GRMS) ranked cyber attack or data breach as their number one current and future risk.

Article 5 mins
Our research shows three workforce challenges specific to manufacturing companies. Addressing these is critical to future success.

Article 5 mins
Understanding the physical and transition risks will be key to successfully managing climate risk and developing a climate resilient luxury goods business.

Article 6 mins
Avoid limiting a portfolio’s capacity based on the capabilities or bandwidth of an existing process by working with the right partner.

Article 3 mins
As COP28 approaches, leaders are exploring ways to make their businesses more sustainable and climate resilient.

Article 7 mins
Generative Artificial Intelligence (AI) – a type of artificial intelligence that has the ability to create material such as images, music or text – is already a proven disruptor and its adoption is growing at an explosive rate.

Article 15 mins
A complex macroeconomic environment continues to shape risk strategies and market responses.

Article 12 mins
Medical costs continue to rise around the world. Aon’s Global Medical Trend Rate report provides insight into what conditions are driving these increases.

Article 7 mins
Insurance CEOs are well aware of the talent crisis: they’re fully engaged and seeking answers.

Article 6 mins
With increasing ransomware attacks, building resilience is a top concern for business leaders.

Article 6 mins
Insurance leaders can confidently future-proof their business strategy and avoid misalignment, by engaging the right groups of people to define and deliver their roadmap for success.

Article 6 mins
Commodity Price Risk or Scarcity of Materials is the seventh biggest risk facing organizations globally today and is predicted to rise to the third most critical risk by 2026, according to our survey.

Article 4 mins
Economic Slowdown or Slow Recovery is the third biggest risk facing organizations globally today, and is predicted to be the second most critical risk by 2026, according to our survey.

Article 5 mins
Failure to Attract or Retain Top Talent is the fourth biggest risk facing organizations globally, and is predicted to remain the fourth most critical risk by 2026, according to our survey.

Article 5 mins
Regulatory or Legislative Changes are the fifth biggest risk facing organizations globally today, and are predicted remain the fifth most critical risk by 2026, according to our survey.

Article 4 mins
Supply Chain or Distribution Failure is the sixth biggest risk facing organizations globally today, and is predicted to fall to the thirteenth most critical by 2026, according to our survey.

Article 4 mins
Business Interruption is the second biggest risk facing organizations today and is predicted to fall to the sixth most critical by 2026, according to our survey.

Article 7 mins
Cyber Attack or Data Breach is the number one risk facing organizations globally and is predicted to remain in this position by 2026, according to our survey.

Article 4 mins
Damage to Brand or Reputation is the eighth biggest risk facing organizations globally today and is predicted to fall to rank twenty one by 2026, according to our survey.

Article 5 mins
Failure to Innovate or Meet Customer Needs is the ninth biggest risk facing organizations globally today and is predicted remain in that position by 2026, according to our survey.

Article 4 mins
Increasing Competition is the tenth biggest risk facing organizations globally today, and is predicted to rise to the seventh-most critical risk by 2026, according to our survey.

Article 11 mins
Gene and cell therapies represent breakthrough advances in medicine, but they also have significant costs and potential risks for patients, employers, insurers, governments and manufacturers.

Article 9 mins
A global survey of medical trend expectations highlights the health conditions affecting employees and impacting costs, how employees are using their medical plans, areas where they need better coverage and where employers can build on these insights.

Article 11 mins
In the wake of record-breaking high global temperatures in 2023, the rising frequency of extreme heat due to climate change creates an urgency for the risk industry to analyze climate trends for better risk mitigation.

Article 6 mins
Life sciences companies lag other industries in addressing the physical and mental health of employees and getting them future-skills ready. Here are actions to address these gaps.

Article 12 mins
(Re)insurers must embrace AI technology to successfully navigate today’s emerging transformative trends that are shaping the insurance landscape.

Article 6 mins
A drug class known as GLP-1 receptor agonists or simply “GLP-1s” (e.g., Novo Nordisk’s Ozempic) has been used for several years to help control type 2 diabetes.

Article 6 mins
Technology, media and communications businesses need to understand how climate change threatens their operational resilience. Parametric insurance is becoming an important part of the solution.

Article 6 mins
Within the fast-moving Technology, Media and Communications sector, workforce resilience is critical to operational resilience. The journey there involves understanding the key components of workforce resilience, how they can be measured and what initiatives promote greater resilience.

Article 6 mins
Everyone working for an organization is responsible for building a culture of cyber resilience.

Article 8 mins
Creating the right mix of talent will be key for capturing (re)insurance growth opportunities as transformative trends shape the future landscape.

Article 11 mins
With medical costs continuing to rise globally, Aon’s 2024 Global Medical Trend Rates Report examines the risk factors driving the increased costs.

Article 7 mins
New pay transparency laws are forcing employers to develop a pay disclosure strategy and make decisions like whether to voluntarily disclose salaries where it’s not legally required.

Article 9 mins
The strategic use of credit solutions (credit insurance, political risk insurance and surety) can enhance liquidity, improve transaction returns, facilitate capital-efficient deal closures, and support long-term value creation.

Article 7 mins
Employers that build flexible, inclusive cultures help caregivers in the workplace to balance their responsibilities on the job and outside work.

Article 11 mins
The SEC published nine new Compliance and Disclosure Interpretations (C&DIs) covering the pay versus performance rule. The C&DIs focus on when awards are considered vested and the valuation of equity awards in specific circumstances.

Article 9 mins
As the need for climate-resilient infrastructure grows, the industry contends with changes in regulations, building strategies and risk.

Article 8 mins
CHROs are using workforce data and insights to craft solutions that address organizational challenges and elevate their people.

Article 9 mins
Burnout and languishing threaten individual and organizational productivity and business outcomes. A company’s employee wellbeing strategy can help prevent them by mitigating microstress.

Article 8 mins
With continued market volatility, finding adequate coverage for growing protection gaps via traditional insurance alone is challenging. Parametric solutions can help businesses build resiliency against catastrophe-prone exposures and more.

Article 6 mins
A holistic understanding of climate risks requires a multidimensional approach to data, risk models and developing staff expertise.

Article 5 mins
The IAC recommends the SEC mandate prescriptive requirements in several key areas of human capital management disclosures to provide investors with relevant, timely and comparable data to adequately contextualize a company’s workforce value.

Article 7 mins
New legislation is presenting employers with an opportunity to model sustainable pensions and modernize employment conditions.

Article 8 mins
With a robust exit strategy, financial sponsors can create value from day one and enable a strong long-term outlook.

Article 6 mins
As cyber attacks become more sophisticated, banks can shore up their cyber-security resilience efforts by building a partnership between business leaders and cyber technologists.

Article 10 mins
As cyber threats continue to increase it is vital that businesses build ongoing operational cyber resilience to help assess, mitigate and transfer risk, and recover should an attack occur.

Article 9 mins
Addressing the retirement pay gap issue between men and women starts with first acknowledging it exists. Then companies can conduct further analysis and adjust their benefit plans accordingly.

Article 5 mins
Secondary deal activity will likely continue to strengthen as financial sponsors navigate widespread macroeconomic uncertainty.

Article 8 mins
Organizations can refresh their employee pension communications with these five tips to help people connect with their retirement planning.

Article 9 mins
The first 10 days after a cyber-attack can be the most damaging. Having a cyber incident response plan in place and ready to deploy can help companies assess threats and develop controls.

Article 6 mins
Pricing pitfalls are more common than you think, whether it's working with incomplete data or key man risk – but with the right pricing process, many of these issues can be mitigated. Read our article to learn about the most common pricing errors, and what insurers can do about it.

Article 5 mins
In today's increasingly complex insurance landscape, an inadequate pricing system can not only impact insurers' view of risk, but also prevent them from making the right decisions at the right time. Read our article on why it's essential to get pricing right.

Article 7 mins
By leveraging the advances made by academic research, companies can develop more robust climate risk resilience.

Article 6 mins
Climate modeling has been around for decades but mainly used by academic and government scientists. Led by the risk industry, the private sector is adapting these models to broadly assess the physical impacts of climate change.

Article 9 mins
With the continued threat of rising temperatures, companies should focus on building climate and weather-related impacts into their overall workforce resilience plans.

Article 9 mins
Companies recognize that wellbeing is more important than ever. But the programs they offer don’t always match what their employees need.

Article 4 mins
SECURE 2.0 is changing retirement planning for businesses and employees. Strategic decisions will be critical in building sustainable retirement plans.

Article 5 mins
Sales teams have unique compensation programs that are critical for aligning selling behavior and outcomes to business goals. Here are five considerations to prepare plans for the year ahead.

Article 4 mins
As cyber attacks evolve, insurers are scrutinizing how organizations understand and address potential cyber security exposures. Achieving a baseline of security standards is crucial to securing coverage, demonstrating a strong resiliency program is key to achieving optimal terms and conditions.

Article 6 mins
Not only does ESG regulation have the potential to make or break an M&A deal, but failure to comply could also significantly damage a business.

Article 11 mins
Companies are increasingly turning to personalization to keep up with workforce changes and deliver value to their employees.

Article 11 mins
In a move designed to close the gender pay gap, the European Commission is increasing pay transparency across member states. Prepare your firm now for potential implications and opportunities.

Article 5 mins
Climate change or exposure growth? By understanding the drivers of increased severe convective storm loss volatility, reinsurers can better prepare for January 1 renewals.

Article 7 mins
Innovation in data, analytics and risk transfer solutions enables Aon to help clients accelerate their investments in decarbonization and climate resiliency and support the transition to a lower-carbon economy.

Article 7 mins
Alternative proteins and farming methods may be the future of food, but stakeholders must be aware of the risks that come with these opportunities.

Article 9 mins
In a volatile climate, institutional investors are turning to outsourced chief investment officers to conquer administrative, regulatory and market challenges.

Article 6 mins
With the property market remaining volatile, risk buyers need a solid strategy to stabilize their risk portfolio.

Article 6 mins
An OCIO can help asset owners make decisions with confidence and help deliver an optimal investment strategy.

Article 6 mins
Many risk buyers remain challenged to find adequate coverage to address a growing protection gap, especially for their cat-prone exposures and other risks. Parametric is an alternative solution that has grown in utilization to insure against a variety of perils in any market conditions.

Article 9 mins
Cyber security is a growing business concern, but many companies still need to improve their cyber resilience in key areas. Aon’s 2023 Cyber Resilience Report explores how global industries are protecting themselves against cyber threats.

Article 9 mins
A strong people strategy and robust change management and communication approach will drive better cultural alignment during M&A deals — ultimately increasing the chance for success.

Article 7 mins
In a rapidly changing IP landscape, companies should consider assessing their risk exposures and management strategies to help protect some of their most valuable assets.

Article 8 mins
As cyber attacks increase and become more costly, cyber security coordination across business units has become more important than ever. By bringing the chief information security officer (CISO) and chief risk officer (CRO) together, companies can take a proactive approach to minimizing cyber risks.

Article 8 mins
As healthcare becomes more expensive, companies are searching for ways to keep costs down for their employees. Focusing on a few core areas can help.

Article 7 mins
Business leaders are facing a growing number of complex and interconnected risks, resulting in decision fatigue for many executives. Aon CEO Greg Case explains how leaders can take a proactive approach to difficult choices while investing in talent development and wellbeing.

Article 9 mins
Artificial intelligence is driving rapid change globally. In technology, media and telecoms, AI can be a human capital opportunity, not just a risk.

Article 7 mins
Delivering compelling total rewards that meet the needs of a diverse workforce requires a strong connection to your EVP and innovative technology.

Article 7 mins
Work-from-home and hybrid-work models can significantly influence the commercial real estate market, which in turn has a major influence on the financial health of a city.

Article 7 mins
Employees often face cyber attacks while they’re on travel for business, putting sensitive company data, trade secrets and intellectual property at risk.

Article 8 mins
Risk managers are rethinking their risk resilience by turning to parametric insurance, an “if-then” model designed to complement and supplement a traditional indemnity program and better match capital to the broad nature of risk caused by natural disasters.

Article 9 mins
Exploring the human capital challenges in the Middle East arising from the current interest rate environment.

Article 8 mins
Employer-provided retirement programs have become more complex to administer. Collective plans can help to ease the burden.

Article 7 mins
To maintain a competitive edge in today’s complex global economy, people leaders must expand their data strategies and get organized to keep up-to-date and make better risk decisions.

Article 6 mins
The return of El Niño is creating challenges for the global supply chain, including risks for transportation and logistics. As disruptive weather and climate events persist, vulnerable industries will need to rethink their supply chain strategies to maintain resilience.

Article 7 mins
An alarming number of insured Americans still can’t afford healthcare treatment, but there are approaches employers can take to reduce costs and improve outcomes for employees and their families.

Article 5 mins
Record high Atlantic water temperatures are leading forecasters to predict an above-average hurricane season. Learn how to build business resilience to protect hurricane-prone properties.

Article 8 mins
AI is creating new possibilities in life sciences, especially in R&D, training and marketing. But, as the industry adapts to AI, it also faces risks and challenges.

Article 14 mins
Unexpected global changes have shaken supply chains, exposing the fragility of a complex system. While some businesses search for stability, others are harnessing the power of improved data, analytics and AI to strengthen their resilience and opportunities for growth.

Article 8 mins
Lowering greenhouse gas emissions is a growing priority, but successful industrial decarbonization requires a clear view of regulations and risk.

Article 5 mins
In a tight labor market, people leaders are relying more on talent assessments for pre- and post-hire candidates. The resulting data and insights lead to more informed hiring and retention decisions.

Article 8 mins
As patent litigation continues to evolve worldwide, analyzing past trends can help support informed risk management decisions for the future.

Article 6 mins
New standards from the IFRS Foundation’s International Sustainability Standards Board (ISSB) add expectations for companies to disclose more stringent climate risk and oversight information, as well as greenhouse gas emissions data.
Article 6 mins
Artificial intelligence could help banks make better use of customer data and workforce capabilities, in addition to reducing financial fraud. However, financial institutions must be mindful of the risks of AI as well.

Article 6 mins
As the risk landscape expands, every TMC business should consider developing a robust framework for operational resilience. A three-phase strategy provides a rational approach to building a framework to help understand and manage key risk concerns and minimize business disruptions.

Article 6 mins
Working together across an organization to build a contingency plan for dangerous climate events is crucial to ensuring everyone is protected.

Article 7 mins
Companies can enhance their DE&I efforts — and gain better returns — by creating a culture that enables their employees to feel a sense of belonging at work.

Article 5 mins
In a constantly evolving business landscape, talent assessments can help organizations understand current and future skills gaps in their workforces.

Article 9 mins
To maintain a competitive edge in today’s fast-paced and volatile world, HR leaders must harness the power of their people data.

Article 6 mins
Without the proper insurance, litigation and contingent risks can lock up capital and prevent a deal from closing.

Article 7 mins
Wellbeing strategy, once seen as a luxury, is now a vital part of a company’s overall strategy. Integrating wellbeing into other areas of a company is the next step forward.

Article 14 mins
Protecting and sustaining businesses in food, agribusiness and beverage, financial institutions, life sciences and renewables require a resilient workforce. Organizations must consider the skills, capabilities, agility and wellbeing of their people to achieve a productive and healthy workforce.

Article 7 mins
Above-average starting salaries for new employees are leading to 'pay compression.' And it could pose a threat to pay equity.

Article 11 mins
A buyer-friendly Cyber and E&O market is quickly emerging. Learn more about the changing global market and how to capitalize on it.

Article 9 mins
Uncovering the impact of the UK Gender Pay Gap reporting regulations

Article 5 mins
A ROSI framework allows businesses to link risk, security and insurance to help manage cyber exposure and increase cyber resilience.

Article 6 mins
In today’s increasingly volatile global economy, business leaders are focusing on two key areas of decision-making: Risk Capital and Human Capital.

Article 10 mins
Pressure to reduce costs in response to a challenging economic environment highlights the pivotal role data and analytics can play in optimizing business investment in talent and future growth.

Article 7 mins
The current economic climate has created headwinds for mergers and acquisitions, causing shifts in financing. Using trade credit insurance can help unlock value and reduce volatility.

Article 9 mins
M&A deals are among the most challenging events a business can navigate. Effective organization design and talent planning are critical to ensure a smooth transition.

Article 7 mins
The LPGA shares how data technology has helped to pinpoint the personality traits of top players, leading to success on and off the golf course.

Article 6 mins
With increasing global uncertainty, businesses should focus on emerging threats and decide how to best address them.

Article 12 mins
Resilience and growth are dependent on business leaders taking action to respond to ESG risk and opportunities.

Article 6 mins
Return on investment is one of the biggest considerations in implementing employee benefits. This is more pertinent as global economic volatility forces companies to balance costs with expectations.

Article 7 mins
Where, when and how work gets done is changing, causing companies to reassess existing roles and determine what skills are required for the future.

Article 7 mins
Aon’s 2022–2023 Global Wellbeing Survey explores what employers around the world are doing to support the needs of today’s workforce.

Article 5 mins
Benefit captives support health plan design flexibility and a standard of coverage for all employees.

Article 7 mins
Directors face potential equity transaction liabilities throughout a company’s growth. Learn about mitigating these costly risks.

Article 4 mins
Make your assessment process successful: Meet inclusion and diversity goals. Be mindful of the participant experience. Cater to individual needs.

Article 7 mins
How can corporate buyers achieve optimal placement outcomes given the current reinsurance market dynamics?

Article 6 mins
During a complex M&A deal, centralized project management helps keep human resources workstreams connected to ensure successful post-deal outcomes.

Article 6 mins
New regulations in the U.S. aim to peel back the curtain on how healthcare prices are set. This will drive employers to use data to make better decisions about the best coverage for their people.

Article 12 mins
The rising cost of energy is driving leaders in the heavy industries to rethink their approach to risk.

Article 6 mins
Increased use of secondary transactions in the private equity market has created an opportunity for Representation and Warranties insurance.

Article 6 mins
As the role of managers changes, organizations are finding new ways of effective manager training.

Article 7 mins
Business leaders should take a close look at their reward programs during a merger or takeover to help retain talent and ensure a cohesive pay strategy.

Article 5 mins
How can leaders build a strong and adaptable supply chain for business survival and growth during uncertain times?

Article 7 mins
To make the most out of their ESG data, companies can draw on different approaches to benchmarking and increase their attention to governance.

Article 6 mins
As healthcare organizations digitalize their business and face global workforce shortages, our analysis finds they are rapidly recruiting new talent with specific data skillsets.

Article 7 mins
How can executives and deal teams execute deals with cyber due diligence and create a competitive advantage?

Article 9 mins
Now more than ever, the reinsurance industry needs insight. But it is still slow to implement advanced data and analytics.

Article 7 mins
How can firms stay on top of cyber threats in an increasingly digitalized world?

Article 11 mins
HR can make an impact in a business by identifying the forces creating instability and linking HR processes.

Article 10 mins
Some of the worst cyber incidents come from the inside. Use these tips to recognize and mitigate insider threats.

Article 13 mins
The renewable energy industry is facing unique headwinds, but there are opportunities to accelerate the role of European onshore and offshore wind power.

Article 7 mins
For many companies, recognizing and addressing supply chain risk can seem like an impossible task. But a unified approach can chart a clearer course of action.

Article 4 mins
While market volatility has decreased the value of 401(k)s, pooled employer plans can produce savings.

Article 7 mins
Employers around the world are seeking ways to prioritize DE&I in their benefits programs and workplace resources, according to Aon’s 2022 Global Diversity, Equity and Inclusion Survey.

Article 7 mins
ESG ratings don’t always tell the whole story, which is why companies should develop a clear and compelling ESG story for D&O underwriters.

Article 7 mins
Life sciences companies are trying to find a balance between navigating economic pressures and a push to innovate for the future.

Article 8 mins
Multifactor authentication is a critical cyber defense, yet criminals are working to bypass it. Use these tips to build an effective MFA layer.

Article 9 mins
Recent events have helped unite security and technology professionals in the fight to thwart cyber criminals. Here's why HR leaders also play a major role.

Article 4 mins
Insurers can help advance a climate crisis solution. Here are three ways the industry can help accelerate the journey to net zero emissions.

Article 13 mins
Industry leaders in life sciences, financial institutions, technology, media and communications and food, agribusiness and beverage face a surge in cyber threats and data breaches.

Article 7 mins
The impact of climate change on businesses, insurers, and communities can provide insight on how to mitigate the risks associated with extreme weather events.

Article 11 mins
Following a tumultuous two weeks in the banking sector and subsequent volatility to global banking markets, depositors and affected third parties are having to rapidly assess, and respond to, a range of risk management, liquidity and human capital challenges.

Article 7 mins
The food, agriculture and beverage sector is examining sustainable solutions and environmentally friendly practices to ensure a resilient future.

Article 4 mins
Volatility in the global economy is putting pressure on organizations and employees at all levels.

Article 8 mins
IP litigation risk continues to evolve year-over-year, creating complex challenges for SMEs. You can help stay protected and prepared by focusing on these mitigation techniques.

Article 2 mins
In the wake of Hurricane Ian, Aon sent a team of experts to the affected area to understand the lessons learned from this storm.

Article 2 mins
HR leaders are at the center of activating ESG initiatives in the workplace. This has a critical impact on protecting a firm’s greatest asset — its people.

Article 7 mins
Businesses are recognizing the need to adapt to the impact of climate change on supply chains.

Article 5 mins
Facing natural disasters, advanced weather and catastrophe modeling can help companies prepare — often resulting in quicker claims processing and response.

Article 5 mins
Climate change has a negative impact on employee health and wellbeing. More employers are addressing these challenges.

Article 7 mins
Today’s global tax environment grows ever more complex. Tax insurance is a potential solution to help provide certainty and protect value in M&A transactions.

Article 5 mins
Academic research collaboration with the insurance industry enhances understanding and creates actionable climate change insights.

Article 6 mins
ESG strategies are becoming a key part of the corporate landscape as executives and investors use new metrics to assess a company's long-term success.

Article 6 mins
Ransomware attacks have become more frequent and costlier, presenting new challenges to business continuity and security.

Article 6 mins
Experts discuss the challenges and opportunities faced by organizations in their journey to net-zero in the Aon Insights Series 2022 in London.

Article 7 mins
In the constantly evolving M&A market, companies must be prepared to navigate a range of risks that can impact the success of their deals.

Article 6 mins
The goal of achieving ‘net zero’ emissions is gaining momentum as a solution to climate change.

Article 8 mins
Governments around the world are seeking to address critical needs and stimulate their economies following the COVID-19 pandemic.

Article 7 mins
The life sciences industry is facing a dynamic and volatile landscape due to the COVID-19 pandemic and other global risks.

Article 11 mins
How can private companies best prepare the ground for a successful US IPO?

Article 12 mins
Climate disclosure requirements will increase globally in 2023. Use this guide in preparation to reduce risk and attract investors.

Article 7 mins
A report by Aon has advised businesses to prepare for a recession by evaluating their workforce, markets and investments.

Article 6 mins
Accompanying the considerable growth and potential, there is a long list of risks associated with the cryptocurrency and metaverse markets.

Article 4 mins
Inflation caused by economic uncertainty and supply chain disruptions has impacted businesses and consumers globally.

Article 7 mins
By investing in biodiversity alongside other climate strategies, companies can find new opportunities and manage risk.

Article 5 mins
NFTs are digital ownership records that are verified using blockchain technology and can be tied to works of art, collectibles and other intellectual property.

Article 8 mins
Reputation analytics are a powerful predictive tool in gauging near-term ESG risk exposures.

Article 6 mins
Data brokers are companies that collect and sell personally identifiable information to third parties. This industry has become a multibillion-dollar industry, but it also presents risks to individuals and businesses whose personal information may be used for nefarious purposes.

Article 6 mins
Because Russia and Ukraine are responsible for a significant share of the world's wheat, barley, corn and oil seed, the conflict will have significant consequences on global food supply and prices.

Article 7 mins
In this interview, Greg Case, the CEO of Aon, discusses the challenges that businesses are facing due to the pandemic, cyber risks, and the impacts of climate change.

Article 6 mins
Credit insurance allows businesses to protect income streams and build resilience. Read more about the different types of credit insurance models.

Article 6 mins
As the global economy becomes increasingly complex, the need for an organization to innovate is brought into sharper focus.

Article 8 mins
A successful DEI strategy is an organization-wide effort and involves effective communication to stakeholders inside and outside an organization.

Article 7 mins
A record number of workers are quitting jobs and changing companies — or thinking about it. How can employers retain talent in today’s competitive market?

Article 5 mins
The rise of non-fungible tokens has created new markets.

Article 8 mins
From working on the front lines and extra childcare needs to losing jobs, women are bearing the brunt of COVID-19’s impact on the workforce.

Article 3 mins
How technology can help solve the difficulties organizations face analyzing data

Article 7 mins
Employee wellbeing has a direct impact on company performance and customer satisfaction.

Article 6 mins
Allyship creates an inclusive workplace where everyone has opportunities for growth and development.

Article 6 mins
Businesses that rely on client relationships face challenges in succession planning as key employees retire or leave the firm.

Article 5 mins
The Suez Canal blockage highlighted the importance of businesses understanding their supply chains and finding weak links to reduce risks.

Article 7 mins
Artificial intelligence is changing the way businesses operate. As its use becomes more widespread, leaders need to understand how this technology works and what its future role may be.

Article 7 mins
Building a resilient workforce for businesses is more important than ever — particularly in the context of the COVID-19 pandemic.

Article 6 mins
For many companies, today’s economic environment and recent banking activity present new ways to think about and manage their investments. Hedge funds can help in diversifying portfolios, if used strategically.

Article 8 mins
The aviation industry was one of the hardest hit by the COVID-19 pandemic. Now it is essential that airlines seize new opportunities.

Article 6 mins
The move toward greater pay transparency will have an impact on the salary considerations of employers and employees alike.

Article 6 mins
This article discusses the importance of good judgment in leaders when making crucial decisions for their organizations.

Article 4 mins
In Uganda and Rwanda, hundreds of small farmers are producing coffee and tea but can’t gain access to major international markets to sell their crops.

Article 5 mins
Aon and Red Cross have joined forces to help communities become more resilient to natural disasters, climate change and public health crises.

Article 6 mins
The value of intangible assets, such as IP, can make up a large portion of a company's market value.

Article 6 mins
A diverse workforce has become a factor that can give an organization the edge in today’s highly competitive business environment.

Article 9 mins
Middle-market businesses — companies with $10 million to $1 billion in annual revenue — play a vital role in driving global economic growth.